
M4 MacBook Air base model – The One Regret I Didn’t Expect
M4 MacBook Air base model owners, gather ‘round. I did the thing a lot of us swear we won’t do—I walked into release week and grabbed the cheapest configuration. No hesitation. No spreadsheet. Just vibes and a credit card. The first hour felt like meeting an old friend: that cool aluminum finish, razor‑thin silhouette, instant wake, the usual Apple “ta‑da.” Then real work hit—photo batches, rough‑cut video, way too many tabs—and the machine stayed whisper‑quiet while cruising. That’s when I realized: the base spec absolutely slaps… except for one tiny, stubborn detail we’ll get into. (Spoiler: yep, storage.) Quick story. I once edited a launch clip on a midnight flight with a previous Air, juggling a camera card, a portable...
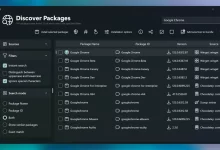
UniGetUI — 27 Brilliant Wins & Pain Points: The Ultimate Power Guide
UniGetUI is the Windows package manager GUI a lot of folks don’t realize they’ve been missing. If you’ve ever bounced between winget, Chocolatey, and Scoop commands—or if you’re the “I just want a clean UI to install, update, and remove software” type—this review and how‑to is gonna save you time, clicks, and those random late‑night update marathons. I’ll break down the good, the bad, the “it depends,” and then walk you through everything from installation to pro workflows. UniGetUI in a Nutshell: Why It Exists and What It Actually Does Under the hood, Windows has multiple ways to install apps programmatically. The command line is powerful but not always friendly. UniGetUI sits on top of those toolchains and gives...

Self-Hosted LLM: 37 Unbreakable, Field‑Tested Plays That Make Private AI Actually Work
Self-hosted LLM projects feel glamorous on slide decks and downright messy in a closet at the back of an office. This guide is for the closet. I’m gonna give you the parts that break, the moves that actually help, and the gritty details teams forget until a pager goes off. I’ve stood in that closet—dust filter in one hand, clamp meter in the other—trying to shave 80 ms off a reply that must feel instant. A quick personal anecdote. Last winter I was helping a scrappy retail team bring a self-hosted LLM online for in‑store product Q&A. We had a friendly model, neat prompts, and a cute kiosk. Day one, lunch rush hit. The queue spiked, the GPU thermaled, the...
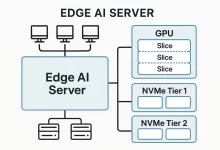
Edge AI Server: 33 Unstoppable, Field‑Tested Moves for Real‑Time Inference That Actually Works
Edge AI server builds aren’t just “mini data centers.” They’re stubborn little race cars that live in closets, back rooms, or branch offices where the Wi‑Fi is moody and the power budget is a punchline. I’ve shipped, babysat, and occasionally resuscitated these boxes for clients who needed milliseconds, not marketing. What follows is a boots‑on‑the‑ground playbook—hardware picks, power math, cooling gotchas, deployment recipes—for making an edge AI server that answers fast and doesn’t melt when the afternoon sun hits the drywall. Quick anecdote: one rainy Friday I slid a brand‑new node into a 12U rack wedged behind a printer the size of a hatchback. We fired up a real‑time vision pipeline; everything looked good. Twenty minutes later? Thermal throttle city....

iPhone 17 Pro aluminum frame – 2 Key Reasons Behind Apple’s Titanium U‑Turn
iPhone 17 Pro aluminum frame has been floating around the rumor mill for months, and I’ll be honest—I didn’t buy it at first. Apple just spent two flagship cycles flexing titanium. The look. The feel. The whole “premium” thing. Then a friend in product design poured coffee over my skepticism and said, “If the mission shifts to cooler chips and lighter pockets, aluminum’s the adult in the room.” I slept on that line, ran the numbers, and yeah—the case for aluminum isn’t just plausible. It’s compelling. Quick anecdote before we go deep: last year I rode a red‑eye home from LA with a 4K edit churning on my phone. Ten minutes into color grading, the device pulled a classic hot‑pocket...
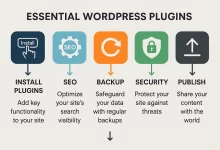
Essential WordPress plugins – 27 Unbeatable Picks + Best‑Combo Stack (2025)
Essential WordPress plugins are the dependable, everyday tools that turn a basic install into a site that feels tight, fast, and trustworthy. No gimmicks—just the pieces that make growth easier. A quick personal story: last spring I rushed a client launch and skipped half my checklist. No cache, no image compression, weak spam filters. The site limped out, editors were frustrated, and Lighthouse looked like a crime scene. The next morning I rebuilt with a lean stack of Essential WordPress plugins, flipped on a real backup, tightened logins, and preloaded the right assets. Traffic held, bounce rate dropped, and the team stopped fighting the site to publish. Lesson learned. Essential WordPress plugins: how this guide works This is a...
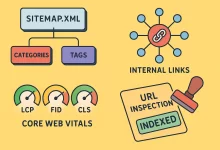
Google Blog Indexing – 6 Unbeatable Wins for Faster Rankings
Let’s be real: getting new posts to show up in Google isn’t magic. It’s systems. Fix crawl paths. Clarify intent. Nudge Google with clean signals. That’s what Google blog indexing is about—teaching search engines your site is alive, useful, and technically sound. I’ve used these exact steps on scrappy side projects and brand new client blogs, and the difference between “invisible” and “found” is night and day. Quick story: a few months back I launched a tiny weekend blog on a bare-bones VPS. First week, nothing. I tweaked my robots.txt, shipped a real sitemap.xml, hardened HTTPS, polished internal links, and requested indexing for key URLs. Two days later, first impressions and clicks rolled in. Not viral—just real. And that little...

Nano Banana — 9 Real-World Ways I Use It Daily
I’m gonna keep this practical. A couple of Sundays ago, I was knee-deep in a photo backlog, coffee going cold, rain tapping the window. I tossed a throwaway shot into Nano Banana, asked for a desk-ready figurine look, and my partner did a double take—“Which studio made that?” That reaction—curiosity + a tiny bit of disbelief—pretty much sums up why I’ve stuck with it. What follows is a fully original, field-tested guide to nine things I do all the time—no fluff, no complicated graphs, just settings, prompts, and gotchas so you can make Nano Banana earn its keep. Where Nano Banana Shines in Real Workflows Nano Banana is strongest when you want believable edits that respect geometry, lighting, and...

OLED Gaming Monitor Review 2025: A Real‑World Field Test for Gamers and Creators
OLED gaming monitor review pieces sometimes read like spec sheets with adjectives. This one’s different. Two months ago I swapped my daily driver to a 27‑inch QD‑OLED, then lived with it—coding at dawn, gaming at midnight, color‑correcting a client video over a weekend that turned into a caffeine experiment. This OLED gaming monitor review is built on that rhythm: real content, real games, real annoyances, and the small wins you only notice after week three. Upfront: I’m not trying to sell you an acronym. I’m trying to help you avoid buyer’s regret. If an OLED looks incredible for your favorite game but gives you eye strain in spreadsheets, you’ll stop using the good parts. The right choice is the panel...

Zero Trust Server Security: A 2025 Field Guide for Real‑World Teams
Zero trust server security sounds grand until you’re staring at a pager at 2:11 a.m. with a blast of failed SSH attempts and a CPU graph that looks like a picket fence. That was me last spring. A forgotten jump box, a stale local admin, and a permissive security group invited trouble. We got lucky—no data moved, the doors slammed shut, and the lessons stuck. Since that night, I’ve been ruthless about small, boring controls that add up to a fortress. What follows is the exact playbook I reach for now, tuned for 2025 realities and written for folks who actually have to run this stuff at 3 a.m. Here’s the vibe: honest tactics, minimal heroics, and lots of receipts....

 FoxDoo Technology
FoxDoo Technology

 FoxDoo Technology
FoxDoo Technology