Server Page 3
FoxDooTech’s Server category offers expert insights into cloud computing, hosting solutions, server infrastructure, data management, and server security trends.

Automation transforms your VMware environment from a manual, error-prone setup into a consistent, repeatable platform that scales with your business. In this guide, we dive deep into scripting and infrastructure-as-code to automate virtual machine provisioning, network configuration, and security hardening. You’ll come away with concrete examples using PowerCLI, Ansible, NSX APIs, and Terraform to streamline operations and enforce compliance. 1. Automating VM Deployments 1.1 PowerCLI for Rapid Provisioning # Connect to vCenter Connect-VIServer -Server vcsa.example.com -User [email protected] -Password 'P@ssw0rd' # Create a new VM from template New-VM -Name "WebServer01" ` -Template "Win2019-Template" ` -Datastore "Datastore1" ` -VMHost "esxi01.example.com" ` -NetworkName "Prod-Net" ` -NumCpu 4 -MemoryGB 8 Best Practices: Use templates with pre-installed VMware Tools and security patches. Parameterize VM names,...

Ensuring smooth, predictable performance in your VMware environment requires more than just throwing hardware at the problem. By carefully allocating resources, fine-tuning settings, and adhering to best practices, you can maximize throughput, minimize latency, and keep virtual machines running at peak efficiency. In this deep-dive guide, we’ll cover: 1. CPU Optimization & Overcommit Management 1.1 Leverage Hardware Virtualization Enable Intel VT-x / AMD-V in BIOS/UEFI for all ESXi hosts. Use Enhanced vMotion Compatibility (EVC) clusters to ensure consistent CPU feature sets across hosts. 1.2 Right-sizing vCPU Allocation Match vCPUs to Workload: Don’t assign more vCPUs than a VM needs—idle vCPUs waste host cycles. Avoid Overcommitment Pitfalls: ESXi can overcommit vCPUs, but keep vCPU:core ratio at or below 4:1 to reduce...

Creating a rock-solid VMware virtualization environment starts with a clean, repeatable installation and follows through with proper configuration. In this comprehensive guide, we’ll walk through every step—from selecting the right VMware edition to launching your first virtual machine (VM). We’ll cover: 1. Edition Selection & Licensing Before you download any software, choose the VMware product that best fits your needs: VMware Workstation Pro (Windows/Linux desktop) Ideal for power users and developers who need advanced snapshot management, shared VM folders, and remote connections. VMware Player (free for non-commercial use) Good for simple VM testing without advanced features. VMware ESXi (bare-metal hypervisor) Best for datacenter deployments. Installs directly on server hardware for maximum performance. VMware Fusion (macOS) Native virtualization on Mac with...

Ubuntu Server 24.04 LTS brings five years of support, performance boosts in Linux 6.8, and built-in container tools. This guide walks you through every command and menu click—from preparing your USB stick to locking down SSH—so you can deploy a production-ready server with confidence. 1. System Requirements & Preparations CPU: 2 cores @ 2 GHz minimum RAM: 4 GB (8 GB+ recommended) Disk: ≥ 25 GB (SSD preferred) Network: Wired Ethernet adapter Boot Media: USB stick (8 GB+) Secondary Machine: To download ISO and write USB Tip: Enable virtualization (VT-x/AMD-V) in BIOS if you plan VMs. 2. Download & Validate the ISO Download wget https://releases.ubuntu.com/24.04/ubuntu-24.04-live-server-amd64.iso Verify Checksum sha256sum ubuntu-24.04-live-server-amd64.iso Compare against the checksum on releases.ubuntu.com/24.04. 3. Create a Bootable USB...

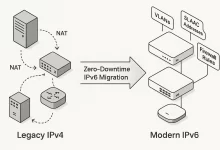
1. Introduction Enterprises worldwide are racing to adopt IPv6 to solve the IPv4 address exhaustion problem and unlock modern networking benefits. This guide walks you through a realistic, zero-downtime migration on Cisco Meraki MX, MS, and MR devices. Each step includes dashboard screenshots (you’ll capture locally), example configurations, validation commands, and troubleshooting tips—so your team can implement IPv6 without guesswork. 2. Planning & Design 2.1. Audit Existing IPv4 Infrastructure Export your current Meraki network report: Dashboard > Organization > Summary report > Export as CSV. Document all VLAN IDs, subnets, DHCP scopes, firewall rules, NAT policies, VPN peers. Create a spreadsheet with columns: Device Serial, VLAN, IPv4 Subnet, DHCP Range, ACLs. 2.2. Design Your IPv6 Address Plan Obtain a /48...

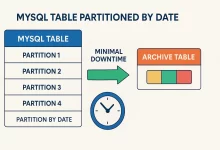
As a database administrator, I once relied on DELETE to purge large volumes of obsolete records. Over time, I discovered this approach caused hidden performance and storage headaches. In this post, I’ll share what I learned about InnoDB’s storage model, the pitfalls of bulk DELETE, and the best practices I now follow. Understanding InnoDB’s Storage Architecture InnoDB stores data in tablespaces, segments, extents (groups of 32 pages), and pages (16 KB each by default). When you delete rows, InnoDB simply marks them as deleted—it doesn’t return space to the operating system. As a result, the .ibd file stays the same size, leaving unused “holes” in your tablespace. My Experiment: DELETE Doesn’t Free Space I created an empty table and saw...

As the person responsible for our company’s IT infrastructure, one of my essential tasks was optimizing our web servers. After much research, testing, and consideration, Nginx emerged as the optimal solution due to its high performance, reliability, and flexibility. Understanding Nginx Architecture and Working Model One aspect that immediately attracted me to Nginx was its highly efficient architecture. Unlike Apache’s thread-based approach, Nginx uses a Master-Worker architecture. Master and Worker Processes The Master process manages global operations: reading configurations, launching worker processes, and overseeing their health. Each Worker process, operating independently, handles client requests using an event-driven model, efficiently managing multiple connections with minimal resource usage. Event-Driven Asynchronous Model Worker processes employ a non-blocking, event-driven model, ensuring quick request handling...

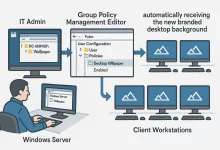
How I Centralized Our Desktop Wallpaper with Active Directory GPO As the IT administrator for one of our corporate clients, I was recently tasked with standardizing the desktop background on nearly 200 domain-joined PCs. Manually updating each machine would be a logistical nightmare, so I leveraged our Windows Server’s Active Directory and Group Policy to automate the process. Scenario & Requirements The client wanted a branded 1920×1080 wallpaper across all employee workstations without touching individual machines. To prepare, I gathered: A high-resolution wallpaper file (1920×1080) to enforce on all desktops. An Active Directory domain controller with file-share capability. Verified AD health (DNS, replication) and appropriate GPO editing permissions. Step 1: Create & Share the Wallpaper Folder On the domain controller:...

Securing Our Linux Servers with SSH Two-Factor Authentication In my role as a systems administrator at our company, I recently observed numerous automated login attempts against our Linux servers. Handling sensitive customer data demands robust security measures, so I decided to implement two-factor authentication (2FA) for all SSH access. Below is the scenario that prompted this change and a detailed walkthrough of how I set it up using Google Authenticator. The Scenario: Why We Needed SSH 2FA Our production environment runs on Debian 12.5 and Ubuntu 24.04 servers hosting web applications and internal tools. After receiving alerts about repeated failed SSH logins, I knew it was only a matter of time before a breach occurred. To mitigate this risk quickly...

One day last week, I woke up to a nightmare scenario: our company’s Apache server had slowed to a crawl, and within minutes it was clear we were under a Distributed Denial of Service (DDoS) attack. Having faced this situation before, I knew immediately what I needed to do. Here’s exactly how I handled it, step-by-step, to not only stop the attack but to make sure it wouldn’t happen again. Step 1: Identifying the Attack The first thing I did was to verify that it was indeed a DDoS attack. I logged into our Apache server and checked the server logs using: tail -n 100 /var/log/apache2/access.log I noticed a massive flood of repeated requests from suspicious IP addresses targeting the...


 FoxDoo Technology
FoxDoo Technology FoxDoo Technology
FoxDoo Technology