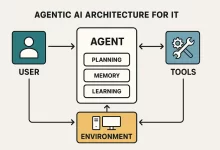
I first felt Agentic AI getting real on a Tuesday night when a flaky API started thrashing our checkout pipeline. Before I even reached for my phone, an agent spun up a canary, rewrote a failing health probe, and dropped an annotated Slack thread with graphs and a rollback plan. I still had to approve the change, but the “plan + diff + blast‑radius” showed up faster than my espresso machine can warm up. That was the moment I stopped seeing agents as flashy demos and started treating them like junior teammates that don’t get tired or ego‑hurt. So this isn’t theoretical. It’s the practical guide I wish I had six months ago—what to build, what to avoid, and how...

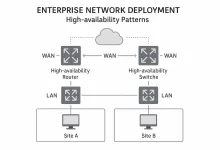
Enterprise Network Deployment gets brutal once gear leaves the warehouse. In this part of the playbook we act as the external managed-service provider who owns every SLA and every panic call—not the client’s internal IT crew. Our mission: transform the signed architecture from Part 2 into blinking LEDs, routed packets, and a cutover that feels boring (because boring means nothing broke). Project Mobilization & Supply-Chain Logistics The clock starts the second the purchase order lands. We immediately spin up a Mobilization War-Room in Jira with three swim-lanes: Procurement + Shipping – track lead times, pallet weights, customs docs. Staging + QA – prep configs, burn-in tests, compliance labels. Field + Cutover – site access windows, lift-gate trucks, hot spares....

Enterprise Network Deployment only gets real when the outsourcing crew’s Sharpie marks become a purchase order. In Part 1 we nailed discovery; now we—an external managed-service provider, not the client’s internal IT squad—must transform raw business objectives into a blueprint that survives board scrutiny, procurement trench warfare, and 3 a.m. failovers. Grab coffee; this is where reputations are forged. Anchor Every Design Choice to Business Outcomes Our outsourcing contracts rise or fall on KPI dashboards, not pretty Visio art. Before a single topology sketch, we lock three driver tables: Revenue-Critical Flows – payment gateway, real-time analytics, click-and-collect APIs. Risk Posture – regulatory penalties, brand damage tolerance, ransomware recovery RTO. Growth Velocity – number of sites per quarter, cloud-migration cadence,...

BitLocker USB encryption has saved my bacon more than once. Last winter I lost a thumb drive in a downtown Vancouver coffee shop—hours later I got it back, but only after the barista admitted snooping. The good news? He saw nothing but BitLocker’s password prompt. That tiny incident reminded me why a locked-down flash drive beats sheer luck every time. Why BitLocker USB encryption Still Matters in 2025 Cloud sync is handy, but millions of pros still juggle code snippets, NDAs, and family photos on portable sticks. A naked USB is basically a suitcase without a lock—it invites prying eyes. BitLocker USB encryption bags military-grade AES-XTS 128-bit (or 256-bit for the paranoid) crypto, hardware-accelerated on most modern CPUs. Drop it,...

Why IT Operations Equipment Still Matters The cloud is cool, but physical IT Operations Equipment remains the bedrock of every SaaS, fintech, and gaming platform I’ve ever helped scale. When a Kubernetes node panics at 3 a.m., you’ll wish you knew exactly which BMC command powers it back on. That’s what this guide is gonna deliver—hands‑on, battle‑tested wisdom for forty‑nine hundred nights of uptime. Compute Tier – The Muscle 1. Physical Servers Classic, beefy x86 or ARM iron. Modern BIOSes speak Redfish, so you can curl -u admin:pass https://bmc.local/redfish/v1/Systems/1/Actions/ComputerSystem.Reset -d '{"ResetType":"ForceRestart"}' from your CI pipeline. Size RAM to avoid swap‑thrash when JVMs spike. 2. Blade Servers Tight on racks? Slide sixteen blades in ten U, attach a liquid‑cooling manifold, and drop...

RustDesk Remote Desktop saved my bacon last winter when our paid tool went into “commercial use detected” lockdown right as I needed to rescue a client’s frozen CAD workstation. One coffee‑fueled hour later I had my own RustDesk Remote Desktop server humming on a cheap VPS, latency under 30 ms, and a very happy customer. Today I’m gonna show you exactly how to do the same—plus eight more tricks to make your setup rock‑solid. 1. Why Choose RustDesk Remote Desktop The open‑source RustDesk Remote Desktop stack delivers end‑to‑end encryption, zero license fees, and total data ownership. You keep the keys, the logs, and the bandwidth. The codebase is split into lean Rust crates—libs/ clipboard for copy‑paste, libs/enigo for synthetic input, and...

Ransomware Defense Tips: 30 Game-Changing Pro Tactics IT Ops Can’t Ignore Confession time. Last winter I watched a customer’s entire file share get blitz-encrypted while their GPUs quietly mined Monero in the background. Not fun. That night I wrote down a ransomware defense tips checklist, and it’s since ballooned into the 30 no-nonsense tactics you’re reading now. 1 – Foundation First: The Bedrock of Ransomware Defense Tips Think of these five basics as the house rules. Ignore them and no fancy AI sensor will save you. Offline, diversified backups. Follow the 3-2-1 gospel—three copies, two media, one off-site. My own Synology backs up to a USB drive that lives unplugged in the closet. ransomware defense tips rule #1. Antivirus or...

 FoxDoo Technology
FoxDoo Technology FoxDoo Technology
FoxDoo Technology