5 Articles
Tags :Network Deployment

Enterprise Network Deployment doesn’t end when LEDs turn green. The real scorecard starts on “Day 2+”—that long haul where uptime, speed, and cost efficiency either make heroes of outsourcing teams or send CFOs hunting new vendors. Building on our Part 3 go-live victory lap and the iron-clad security fabric from Part 4, this final chapter dives deep into the gritty, coffee-fueled world of post-deployment operations. Grab that mug; we’re gonna keep this network humming. Define the Operational Charter: Who Owns What After Go-Live? Before the confetti lands, nail down an Operational Charter that maps every Enterprise Network Deployment component to a named owner and KPI. Our managed-service provider (MSP) contract usually splits duties: MSP NOC: 24 × 7 monitoring,...

Enterprise Network Deployment isn’t truly “done” when the links come up—it’s secure when every hostile packet dies at the perimeter and inside the fabric. After hammering through discovery, architecture, and implementation in Parts 1-3, our outsourced MSP crew now shoulders the heaviest crown: building a security posture that survives auditors, red-team drills, and next month’s zero-day headline. Why Zero-Trust Is Non-Negotiable for Outsourced Deployments When a giant enterprise hires us instead of leaning on its own IT squad, it’s betting that we’ll spot and squash threats faster than an in-house team juggling ten other projects. Zero-trust gives us that edge because identity becomes the new perimeter—users, devices, and apps must prove themselves at every hop. Think of it as...

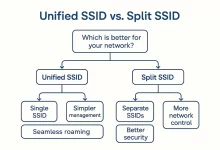
Dual-band WiFi can feel like a magic carpet ride—or a rush-hour traffic jam—depending on one make-or-break choice: do you blend 2.4 GHz and 5 GHz under a single SSID or split them apart? As an IT outsourcing crew that lives or dies on service credits, we’ve watched too many clients face-plant because they copied the default wizard. This guide unpacks the nine fatal traps we keep bailing folks out of and hands you a battle-tested decision blueprint. Preface: The Coffee-Shop Myth Last winter I helped a boutique law firm troubleshoot “random WiFi freezes.” The junior admin swore unified SSIDs were best practice—because that’s how his home router shipped. Cute. Two hours and twenty Wi-Fi analyzers later we discovered every iPhone...

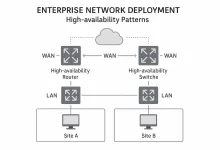
Enterprise Network Deployment gets brutal once gear leaves the warehouse. In this part of the playbook we act as the external managed-service provider who owns every SLA and every panic call—not the client’s internal IT crew. Our mission: transform the signed architecture from Part 2 into blinking LEDs, routed packets, and a cutover that feels boring (because boring means nothing broke). Project Mobilization & Supply-Chain Logistics The clock starts the second the purchase order lands. We immediately spin up a Mobilization War-Room in Jira with three swim-lanes: Procurement + Shipping – track lead times, pallet weights, customs docs. Staging + QA – prep configs, burn-in tests, compliance labels. Field + Cutover – site access windows, lift-gate trucks, hot spares....

Enterprise Network Deployment only gets real when the outsourcing crew’s Sharpie marks become a purchase order. In Part 1 we nailed discovery; now we—an external managed-service provider, not the client’s internal IT squad—must transform raw business objectives into a blueprint that survives board scrutiny, procurement trench warfare, and 3 a.m. failovers. Grab coffee; this is where reputations are forged. Anchor Every Design Choice to Business Outcomes Our outsourcing contracts rise or fall on KPI dashboards, not pretty Visio art. Before a single topology sketch, we lock three driver tables: Revenue-Critical Flows – payment gateway, real-time analytics, click-and-collect APIs. Risk Posture – regulatory penalties, brand damage tolerance, ransomware recovery RTO. Growth Velocity – number of sites per quarter, cloud-migration cadence,...


 FoxDoo Technology
FoxDoo Technology FoxDoo Technology
FoxDoo Technology