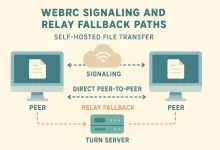
I’m gonna be straight with you—last month a 9 GB 4K video project almost broke me. We chopped it into e-mailable chunks, begged a “premium” cloud drive to hurry up, even tried the ol’ sneaker-net shuffle with a USB stick. Nothing felt right. Then I discovered self-hosted file transfer. I spun up a Docker container, sent my editor a magic link, and—boom—he pulled the entire thing at gigabit speed straight from my browser. No middlemen, no storage caps, no soul-crushing waits. That night flipped my workflow on its head, and in the next few minutes I’m gonna flip yours too. 1. The Pain of Public Cloud Sharing Cloud drives started as life-savers, but boy have the strings multiplied. Throttled free plans,...

I’m gonna be straight with you—few things can bottleneck a shiny new rig faster than the wrong storage. My friend Chris learned that the hard way last winter when his “great deal” QLC drive face-planted mid-Fortnite update. Watching his frame rates crawl lit a fire under me to stress-test every NAND flavor I could grab. The result? This no-fluff dossier on TLC vs QLC SSD tech, spiked with real-world numbers and hard-won anecdotes. By the end, you’ll know exactly which drive belongs in your build, your laptop, your NAS—heck, even Grandma’s photo PC. 1. Flash 101 – What the Extra Bit Really Means TLC vs QLC SSD comes down to bits per cell: TLC stores three, QLC crams in four....

PC build checklist — three little words that separate a flawless fresh rig from a headache-ridden money pit. I learned that the hard way last winter when a friend’s brand-new RTX-rig stuttered like a decade-old toaster because we’d skipped one “minor” post-build tweak. Don’t repeat my pain. Grab a coffee, crack those knuckles, and walk through this PC build checklist with me, step by step. Turns out a lot of builders—myself included—skip the small stuff. A tutorial I skimmed lists simple oversights like using the wrong M.2 slot or flipping a case fan the wrong way, both of which can chop performance in half. Today we’ll dive deeper, slap on some extra engineer-grade detail, and sprinkle in real-world war stories....

It all started with a nasty null-pointer on a client demo day. I tossed the stack trace into Claude, sipped my lukewarm latte, and—bam!—it handed back a patch before the foam collapsed. That moment hard-wired Claude Code efficiency into my daily grind. Below are the fifteen hacks that keep my repos humming; each section dives deep, then shows a side-by-side “Newbie Prompt” versus “Pro Prompt” so you can level-up at your own pace. 1. Warm-Up in the Playground—Master the Interface First The browser playground may look like a toy, but treating it as a gym lets you bench-press bigger code later. Spend fifteen focused minutes tinkering: paste a hello_world.py, toggle “Explain Code,” then swap in “Improve Complexity”. You’ll spot how...

Fastest Web Framework 2025 – Is Astro Really Out-Running Next.js? Confession time: Back in January I rebuilt my side-project blog three different ways on a long weekend just to brag about squeezing out a 95 Lighthouse score. My partner called it “code-surfing”. I call it curiosity – and it kicked off the quest that birthed this monster deep-dive into the fastest web framework 2025 topic. We’re gonna pit Astro 3.8 against Next.js 15 in an unfiltered, no-excuses brawl. I measured raw speed, developer experience, hosting cost, even how future-proof each feels. Buckle up – by the end you’ll know exactly which stack deserves your next green-field build. Why Page-Load Speed Matters More Than Ever in 2025 You’ve heard the stats. Every...

BitLocker USB encryption has saved my bacon more than once. Last winter I lost a thumb drive in a downtown Vancouver coffee shop—hours later I got it back, but only after the barista admitted snooping. The good news? He saw nothing but BitLocker’s password prompt. That tiny incident reminded me why a locked-down flash drive beats sheer luck every time. Why BitLocker USB encryption Still Matters in 2025 Cloud sync is handy, but millions of pros still juggle code snippets, NDAs, and family photos on portable sticks. A naked USB is basically a suitcase without a lock—it invites prying eyes. BitLocker USB encryption bags military-grade AES-XTS 128-bit (or 256-bit for the paranoid) crypto, hardware-accelerated on most modern CPUs. Drop it,...

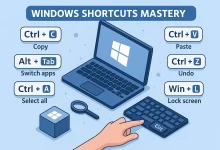
Windows Shortcuts Mastery changed my life one caffeine-fueled night when my mouse died mid-presentation and I survived on Alt + Tab acrobatics. Since then I’ve logged thousands of keystrokes testing, scripting, and (occasionally) abusing every built-in hotkey Windows 11 hides. This guide packs 50 real-world examples—each paired with a plain-English function breakdown—so you can ditch the click-fests and work at warp speed. Why Windows Shortcuts Mastery Still Matters in 2025 Every round-trip from keyboard to mouse costs ~700 ms. Multiply that by 4 000 interactions a day and you’ve burned an hour. These shortcuts shrink UI latency, slash repetitive-strain clicks, and keep your hands on the keys where they belong. Ground Rules: How to Train Shortcut Muscle Memory Practice ten new...

n8n Workflow Integration: The No-Sleep Guide to Embedding Automation Deep in Your Stack If you’ve ever stitched together cron scripts at 2 a.m. while praying the API gods don’t change endpoints overnight, then n8n workflow integration is your new best friend. I’ve rolled it out for a scrappy coffee chain, a 500-seat fintech, and—no joke—my mom’s online crochet shop. Below you’ll find every hard-won lesson I picked up along the way, written so you can hit the ground running instead of face-planting into exception logs. Map the Battlefield Before You Fire a Single Node Picture a whiteboard cluttered with arrows, sticky notes, and half-empty coffee cups—that was my office the day we first scoped a wholesale ERP rollout. Before...

Alienware AW2525HM 320Hz Monitor finally landed on my desk last month, and let me tell you—I haven’t blinked this much since college finals. I hauled the 25-inch beast to a weekend LAN, dialed in 320 Hz, and fragged my buddies so hard they accused me of installing a wallhack. Nope, just the Alienware AW2525HM 320Hz Monitor flexing its muscles. Strap in; I’m sharing a first-hand, caffeine-fueled deep dive that’s equal parts nerdy spec-crunching and seat-of-your-pants gameplay feels. Spec Sheet in Plain English—And Why Each Line Actually Matters Specs are more than marketing bullets—they predict whether a monitor melts your face or merely warms your wallet. So let’s slow-roll every number on the Alienware AW2525HM 320Hz Monitor, unpack the context, and...

Midjourney Prompts: Turning AI Images from Bland to Breathtaking If you’ve ever asked Midjourney for something like, “A majestic castle, epic vibe, 4K,” you know exactly what I’m talking about. The output? Technically flawless—but boring as hell. It’s kinda like listening to elevator music; it fades the second it stops playing. Been there, done that. But what if I told you that your prompts are just too… literal? Yep, that’s right. The key to amazing AI-generated images isn’t simply what you describe, but how you make the AI feel about it. Today, I’m gonna show you how to turn your Midjourney prompts from lifeless descriptions into powerful poetic imagery. Ready? Let’s dive in. Why Emotional Midjourney Prompts Matter Before we...

 FoxDoo Technology
FoxDoo Technology FoxDoo Technology
FoxDoo Technology