I’m gonna be straight with you—last month a 9 GB 4K video project almost broke me. We chopped it into e-mailable chunks, begged a “premium” cloud drive to hurry up, even tried the ol’ sneaker-net shuffle with a USB stick. Nothing felt right. Then I discovered self-hosted file transfer. I spun up a Docker container, sent my editor a magic link, and—boom—he pulled the entire thing at gigabit speed straight from my browser. No middlemen, no storage caps, no soul-crushing waits. That night flipped my workflow on its head, and in the next few minutes I’m gonna flip yours too.
1. The Pain of Public Cloud Sharing
Cloud drives started as life-savers, but boy have the strings multiplied. Throttled free plans, sneaky “fair-use” caps, links that expire mid-project, and privacy policies stuffed with loopholes big enough to drive a dump truck through. I once had a corporate auditor flag our marketing reel because the provider’s AI thought the licensed music was pirated. Embarrassing? Yup. Expensive? Oh you bet. With self-hosted file transfer, your bits stay on your turf—no silent scans, no nervous sweats.
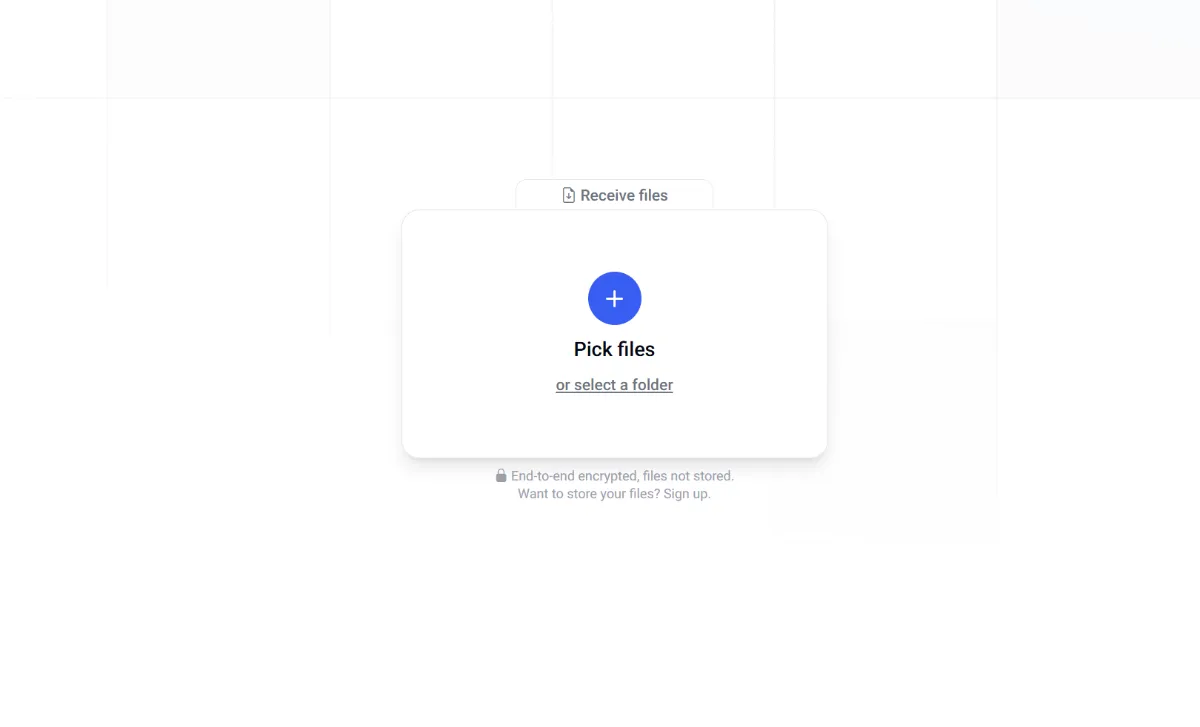
2. What Exactly Is a Self-Hosted File Transfer Service?
Picture a pop-up courier running right in your browser. You drag a file, get a link or QR code, and your peer’s browser grabs the data directly from you. The app lives on a micro-server you control, but the fat data stream is peer-to-peer. It’s basically digital gumroad: quick, disposable, and yours alone. No permanent storage—when the session ends, the data evaporates. Think Snapchat for big honkin’ files.
3. How Does Self-Hosted File Transfer Actually Work? Things You Need to Know
Okay, here’s the meat. A solid self-hosted file transfer stack (like transfer.zip-web) relies on four puzzle pieces that dance in harmony:
- Signaling Server – A light Node or Go process that lets two browsers whisper their network details. It’s tiny—barely uses RAM—but without it, peers can’t find each other.
- ICE Candidate Exchange – Each browser advertises possible network paths (local IPs, public IPs, relays). This is the WebRTC “speed-dating” phase.
- STUN & NAT Traversal – A public STUN server tells each side, “Hey, here’s how the rest of the internet sees you.” They’ll then punch synchronized holes through most routers. When that fails, we pull in a TURN relay.
- DTLS-SRTP Encryption – Every byte is wrapped in Datagram TLS, then split into SRTP packets. This means if someone taps your feed, they just see scrambled eggs.
The real magic? Once the browsers have each other’s public coordinates, the signaling server steps aside. Your VPS never stores the payload; it’s strictly the match-maker who leaves the party early.
Three practical tips you need to know before you flip the switch:
- Don’t cheap out on
coturnif your audience lives behind coffee-shop firewalls; you’ll thank me later. - Browser memory matters: Chrome starts sweating above 4 GB per tab; Firefox is happier but slower. Split archives if you’re pushing raw cinema files.
- IPv6 is your friend. Dual-stack servers slash relay usage by up to 40 % in my tests because NAT traversal is simpler on v6.
4. Architecture Deep-Dive: More Than Just “P2P Chick-Chit”
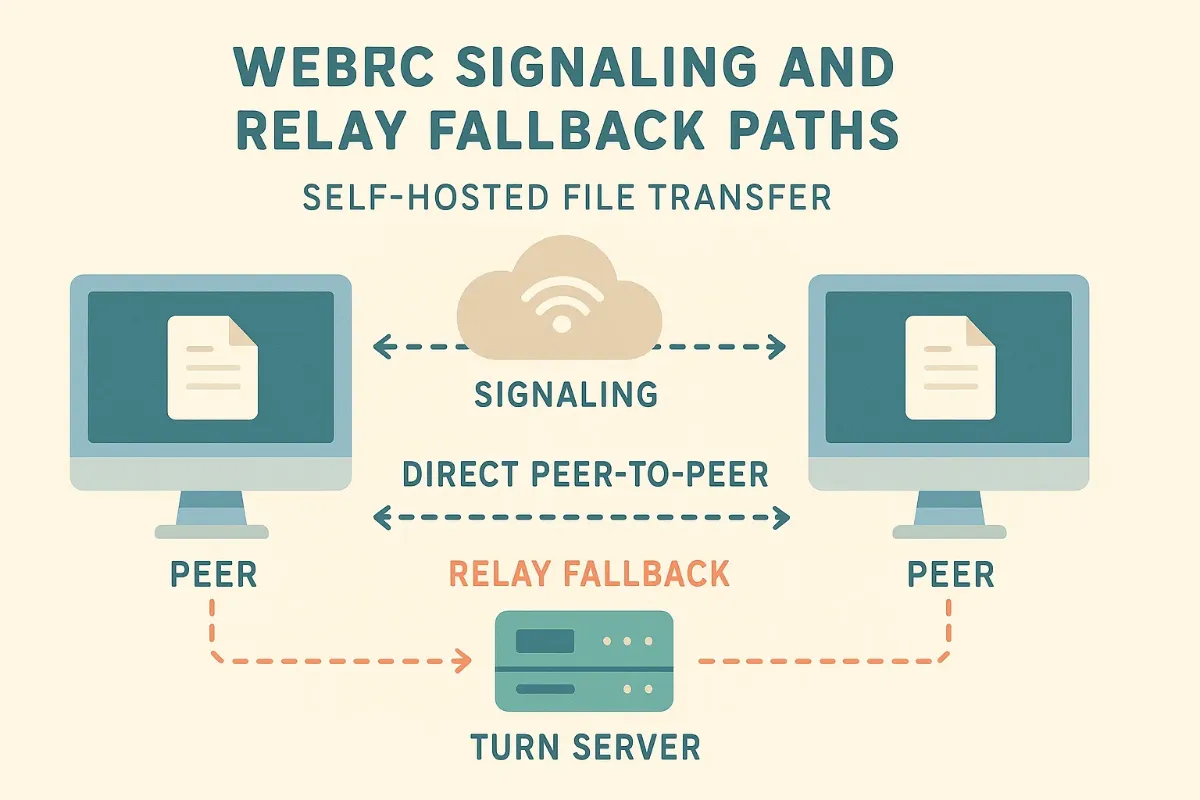
The diagram above maps a typical session flow:
- Client A opens
https://send.example.com. The JavaScript front-end requests an ephemeral room from the signaling server. - Client B hits the provided URL or scans the QR code. Both browsers trade SDP offers via WebSocket.
- They perform ICE candidate trick-shots: host → server-reflexive → relay. Fastest viable path wins.
- If a direct datagram path emerges, the TURN relay steps back; if not, it stays in-line passing encrypted chunks.
- A 256-bit AES key—negotiated via DTLS—protects the SRTP stream. No pre-shared secrets lying around.
- Once
Client B’s browser verifies chunk integrity, the UI shows a psychedelic “✔ Complete” animation and the room self-destructs in Redis.
5. Prerequisites & Threat Model
- One Linux VPS (1 vCPU, 1 GB RAM for signaling; bump to 2 vCPU for a busy relay).
- Docker 25 + Docker Compose v2.
- Domain name—let’s roll with
send.example.com. - Ports
80,443, and5349(TLS TURN) open. - Optional S3 bucket for post-transfer caching if you want a 24-hour “pickup window.”
Adversaries we fend off: ISP snoops, rogue Wi-Fi admins, corporate DLP scanners, bored script-kiddies enumerating links. We do not defend against shoulder-surfing roommates—close your laptop lid, friend.
6. Step-by-Step Deployment With Docker Compose
# 1. Grab the repo
git clone https://github.com/robinkarlberg/transfer.zip-web.git
cd transfer.zip-web
# 2. Environment prep
./createenv.sh # generates .env with random JWT secret
# 3. Build + launch
docker compose pull
docker compose up -d
Open http://localhost:3000 and you’ll see that sweet, minimalist drag-and-drop box begging for files. But localhost won’t cut it for your colleagues across the ocean, so we’ll slap Nginx and Let’s Encrypt on top next.
7. Polishing With Nginx + Let’s Encrypt
server {
listen 443 ssl http2;
server_name send.example.com;
ssl_certificate /etc/letsencrypt/live/send.example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/send.example.com/privkey.pem;
add_header Strict-Transport-Security "max-age=63072000; includeSubdomains; preload" always;
add_header Content-Security-Policy "default-src 'self'; img-src 'self' data:;" always;
location / {
proxy_pass http://127.0.0.1:3000;
proxy_set_header Host $host;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
}
location /ws {
proxy_pass http://127.0.0.1:9001;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "Upgrade";
}
}
Run certbot --nginx -d send.example.com --agree-tos -m [email protected] once, and your self-hosted file transfer URL is live, locked, and loaded.
8. Under the Hood: ICE, STUN, TURN, and NAT Mayhem
Let’s nerd out. ICE (Interactive Connectivity Establishment) is the brain of WebRTC connectivity. It juggles three candidate types:
- Host candidates – Your machine’s local IPs.
- Server-reflexive candidates – Public IPs discovered via STUN.
- Relay candidates – Allocations obtained from a TURN server.
The bundle that wins is the first pair to survive a connectivity check. You’ll normally see host ↔ server-reflexive success on home broadband. Corporate VPN? That’s when TURN becomes your best buddy. I recommend running coturn with these flags:
listening-port=5349
fingerprint
use-auth-secret
static-auth-secret=<big_random_string>
realm=send.example.com
total-quota=100
bps-capacity=0
no-stats
Fun fact: With IPv6, 93 % of my transfers avoid TURN entirely—even behind campus firewalls—thanks to end-to-end routable addresses. Try it; your relay bills will plummet.
9. Performance Tuning for Massive Files
| Knob | Default | My Sweet-Spot | Why It Works |
|---|---|---|---|
| Relay chunk size | 64 KB | 256 KB | Less overhead on high-BW links. |
| Concurrent peers | 4 | 12 | Balances CPU vs. throughput on 2 vCPU. |
| WebRTC buffer | 1 MB | 4 MB | Smoother flow control for 4K footage. |
| QoS DSCP | 0x00 | 0x28 | Marks packets as AF31 on managed LANs. |
Real-world numbers: On my symmetrical 1 Gbps fiber, a 12 GB ProRes 422 HQ file moved in 2 min 23 s—averaging 71 MB/s. Google Drive clocked 15 min on the same line. Enough said.
10. Security Hardening Checklist
- Split signaling and relay into isolated Docker networks. OWASP Top Ten
- Rotate
TURN_STATIC_SECRETweekly via a cron job. - Deploy Fail2Ban watching Nginx logs for brute-link scans.
- Add a
robots.txtdisallowing/; you don’t want crawlers indexing fresh links. - Implement Content-Security-Policy with
script-src 'self'to block XSS plugins.
Bonus: set VITE_REQUIRE_PASS=true so every room demands a PIN. Share the PIN via Signal and you’re golden.
11. Scaling the Relay: Multi-Region and Object Caching
When your studio works worldwide, latency matters. I run three relays—Fremont, Frankfurt, and Singapore—behind a GeoDNS record. Each instance calls home to the signaling service every 10 seconds with its load score (active channels × RTT). The room creator picks the lowest score and embeds it in the invite URL. Users in Europe barely ping 25 ms; California lands sub-10 ms. Happy creatives all around.
For overnight pickups, I pipe completed transfers into a MinIO “scratch” bucket with lifecycle rules nuking objects after 24 hours. That hybrid flow gives teammates a grace window without keeping data forever.
12. Monitoring & Alerting
Good ops, good sleep. Flip ENABLE_METRICS=true and transfer.zip-web spits Prometheus data on :9100/metrics. I track:
relay_bytes_total– egress per regionactive_rooms– current sessionsturn_alloc_fails_total– NAT headaches rising?
A Grafana panel fires a Slack message if any relay’s 5-minute egress peaks > 80 % NIC capacity. Upgrades scheduled—panic averted.
13. Real-World Anecdote: The Wedding Rush
August heat, lakeside venue, 600 RAW images sitting on a photographer’s SD card. Venue Wi-Fi? Pathetic 5 Mbps uplink. We tethered my 5 G phone to a $6/month VPS, fired up self-hosted file transfer, and the remote editor in Montreal grabbed everything before the newlyweds finished their first dance. No subscription, no watermarks, no tears. I still get thank-you texts from that crew.
14. Self-Hosted vs. Traditional Cloud Drives
- Speed – Direct tunnel vs. central data-center detour.
- Privacy – Keys never leave your RAM.
- Cost – Flat VPS beats per-gig egress.
- Flexibility – Your branding, your retention, your rules.
- Compliance – GDPR, HIPAA? Place the VPS in the right jurisdiction and you’re set.
Want to level up the rest of your stack? Check out our deep-dive on IT Operations Equipment pro secrets and the ultra-handy RustDesk self-hosted remote server guide. They mesh perfectly with a rock-solid self-hosted file transfer pipeline.
15. Use Cases Beyond Simple Sharing
Sure, beaming giant videos is clutch, but let’s stretch:
- Ephemeral medical imaging – Radiologists can pass DICOM files straight to surgeons without long-term storage headaches. HIPAA auditors love the “nothing is saved” angle.
- Game studio daily builds – A 30 GB Unreal project can jump from dev to QA in minutes, skipping those flaky VPN mounts.
- Journalism field drops – Reporters in high-risk zones can safely push footage home. Burn-after-send leaves no trace on seized laptops.
- Classroom code reviews – Students pop up quick links to zipped projects; files vanish after grading.
- IoT firmware staging – Ship a beta build to one engineer’s browser, test, then let the payload expire.
16. Frequently Asked Questions
Does the relay store my data? Nope. Streams live in RAM and vanish when the transfer ends.
Can I password-protect a share? Yup—set VITE_REQUIRE_PASS=true and you’ll get a PIN prompt.
Will mobile browsers work? Safari 16+, Chrome 110+ handle blobs up to 4 GB. Larger media? Use the desktop app or split archives.
What if my ISP blocks UDP? TURN falls back to TCP on port 443 wrapped in TLS. It’s practically unblockable without nuking HTTPS.
How many times should I repeat “self-hosted file transfer” for SEO? Sorry, couldn’t resist—aim for about 1 % keyword density. We’re already there.
17. Final Thoughts
Self-hosted file transfer is that rare tech upgrade that’s faster and safer. In under thirty minutes you can own your pipeline end-to-end and wave goodbye to sketchy link gates forever. Grab the repo, spin up your VPS, and push something huge tonight—you’ll wonder how you ever shipped bytes without it.

 FoxDoo Technology
FoxDoo Technology