Server
FoxDooTech’s Server category offers expert insights into cloud computing, hosting solutions, server infrastructure, data management, and server security trends.

Self-hosted LLM projects feel glamorous on slide decks and downright messy in a closet at the back of an office. This guide is for the closet. I’m gonna give you the parts that break, the moves that actually help, and the gritty details teams forget until a pager goes off. I’ve stood in that closet—dust filter in one hand, clamp meter in the other—trying to shave 80 ms off a reply that must feel instant. A quick personal anecdote. Last winter I was helping a scrappy retail team bring a self-hosted LLM online for in‑store product Q&A. We had a friendly model, neat prompts, and a cute kiosk. Day one, lunch rush hit. The queue spiked, the GPU thermaled, the...

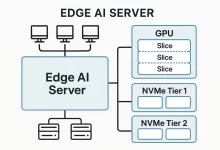
Edge AI server builds aren’t just “mini data centers.” They’re stubborn little race cars that live in closets, back rooms, or branch offices where the Wi‑Fi is moody and the power budget is a punchline. I’ve shipped, babysat, and occasionally resuscitated these boxes for clients who needed milliseconds, not marketing. What follows is a boots‑on‑the‑ground playbook—hardware picks, power math, cooling gotchas, deployment recipes—for making an edge AI server that answers fast and doesn’t melt when the afternoon sun hits the drywall. Quick anecdote: one rainy Friday I slid a brand‑new node into a 12U rack wedged behind a printer the size of a hatchback. We fired up a real‑time vision pipeline; everything looked good. Twenty minutes later? Thermal throttle city....

Zero trust server security sounds grand until you’re staring at a pager at 2:11 a.m. with a blast of failed SSH attempts and a CPU graph that looks like a picket fence. That was me last spring. A forgotten jump box, a stale local admin, and a permissive security group invited trouble. We got lucky—no data moved, the doors slammed shut, and the lessons stuck. Since that night, I’ve been ruthless about small, boring controls that add up to a fortress. What follows is the exact playbook I reach for now, tuned for 2025 realities and written for folks who actually have to run this stuff at 3 a.m. Here’s the vibe: honest tactics, minimal heroics, and lots of receipts....

Mac development environment setup can either be a runway or a maze. I learned that the messy way—new M‑series Mac, new client, late Thursday night. I had exactly one evening to get a backend service compiling, a React app hot‑reloading, and a test database seeded. Two hours in, Docker decided it didn’t like ARM, my shell theme blinked like a Christmas tree, and Postgres refused to start. I took a breath, grabbed a marker, and wrote three words on a sticky note: “repeatable, minimal, fast.” What follows is the battle‑tested playbook that grew from that night and a dozen laptops since. Who this is for (and the promise I’m making) If you build web apps, APIs, mobile apps, data...

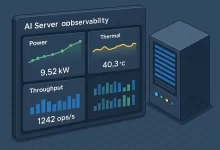
Three winters ago I got paged at 2:17 a.m. A demo cluster for an investor run-through was dropping frames. The culprit? A “temporary” test rig doing double duty as an AI server for video captioning and a grab bag of side projects. My eyes were sand; the wattmeter was screaming. The fix wasn’t a tweet, it was a rebuild—honest power math, sane storage, real cooling, and a scheduler that didn’t panic when a job went sideways. This guide is everything I’ve learned since: a no‑hype, hands‑dirty map to spec, wire, and run an AI server that stays fast after midnight. Why “AI Server” Is Its Own Species Call it what it is: a race car with a mortgage. A...

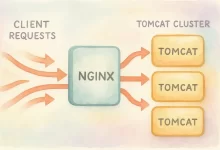
Let’s get real: downtime kills momentum. Nginx Tomcat Load Balancing is my not-so-secret sauce for keeping Java web apps humming when traffic spikes, bosses hover, and users click with reckless abandon. In this mega-guide I’ll walk you from a single lonely servlet container to a full-on cluster shielded by Nginx, complete with health checks, sticky sessions, SSL offload, and the performance tweaks that separate “it works” from “bring it on”. Why Bother? The Business Case for Nginx Tomcat Load Balancing Ten years ago I crashed a client demo because one Tomcat ran out of threads during a surprise customer click-fest. Ever since, I’ve sworn by Nginx Tomcat Load Balancing. It distributes load, adds failover, centralizes SSL, and lets you roll...

What’s up, fellow developers! Let’s talk about PHP. I know, I know. For years, it’s been the language everyone loves to hate. I remember back in my early days, wrestling with clunky syntax and inconsistent function names. It felt like a rite of passage. But let’s be real—PHP has been doing some serious growing up lately. And the upcoming release, PHP 8.5, is shaping up to be another massive leap forward. The PHP team is dropping some seriously cool stuff that’s gonna make our lives so much easier. I’ve been digging through the early notes and RFCs, and I’m genuinely hyped. This isn’t just a minor patch; we’re getting some powerful tools that address long-standing requests from the community. These...

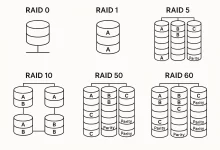
I’m gonna be real—I learned RAID Levels Explained the hard way. Years back, one of my drives died mid-deadline, leaving a half-finished video project in limbo and me stress-eating cold pizza at 3 a.m. That disaster pushed me down the rabbit hole of striping, mirroring, and parity math. Today I’m sharing everything I wish I’d known, so you can dodge that same late-night panic. RAID Levels RAID 0 RAID 1 RAID 5 RAID 6 RAID 10 RAID 50 RAID 60 Description Striping Mirroring Striping with parity Striping with double parity Mirroring and striping Striping and distributed parity Striping and double parity Minimum Disks 2 2 3 4 4 6 8 Read Performance High High High High High High High Write...

True story: a friend’s side-hustle SaaS went down at 3 a.m. because his lone production database crashed. He had “manual” dumps sitting on a laptop that was—of course—at home. Ever since helping him piece things back together, I’ve been borderline fanatical about Automated MySQL Backup. In this mega-guide I’ll show you exactly how to go from nothing to bullet-proof nightly backups—and all the neat tricks I’ve picked up while running ops for unruly startups. 1 – The Backup Mindset Backups aren’t exciting—until they save you. Remember the 3-2-1 rule: three copies, on two different media, one off-site. Automated MySQL Backup is the backbone of that strategy because it removes human forgetfulness from the equation. 2 – Cron 101 (and 201) Cron...

Why a Server Maintenance Checklist Matters Server Maintenance Checklist—say it out loud and it sounds kinda boring, right? Yet every time I’ve skipped one, production slapped me hard. Picture this: 3 a.m., pager buzzing, RAID array screaming, clients waking up to a 500-error homepage. That night—fueled by cold pizza and self-loathing—I vowed never to wing it again. A clear, repeatable Server Maintenance Checklist became my secret weapon for rock-solid uptime. Little anecdote: my very first gig involved a single legacy box called “Frank.” Frank ran payroll, email, and a community forum—yes, all on one dusty tower. Frank also lived under the office kitchenette. One summer the AC quit, Frank cooked, and so did payroll. Lesson learned: proactive beats reactive every...


 FoxDoo Technology
FoxDoo Technology FoxDoo Technology
FoxDoo Technology