Ransomware Defense Tips: 30 Game-Changing Pro Tactics IT Ops Can’t Ignore
Confession time. Last winter I watched a customer’s entire file share get blitz-encrypted while their GPUs quietly mined Monero in the background. Not fun. That night I wrote down a ransomware defense tips checklist, and it’s since ballooned into the 30 no-nonsense tactics you’re reading now.
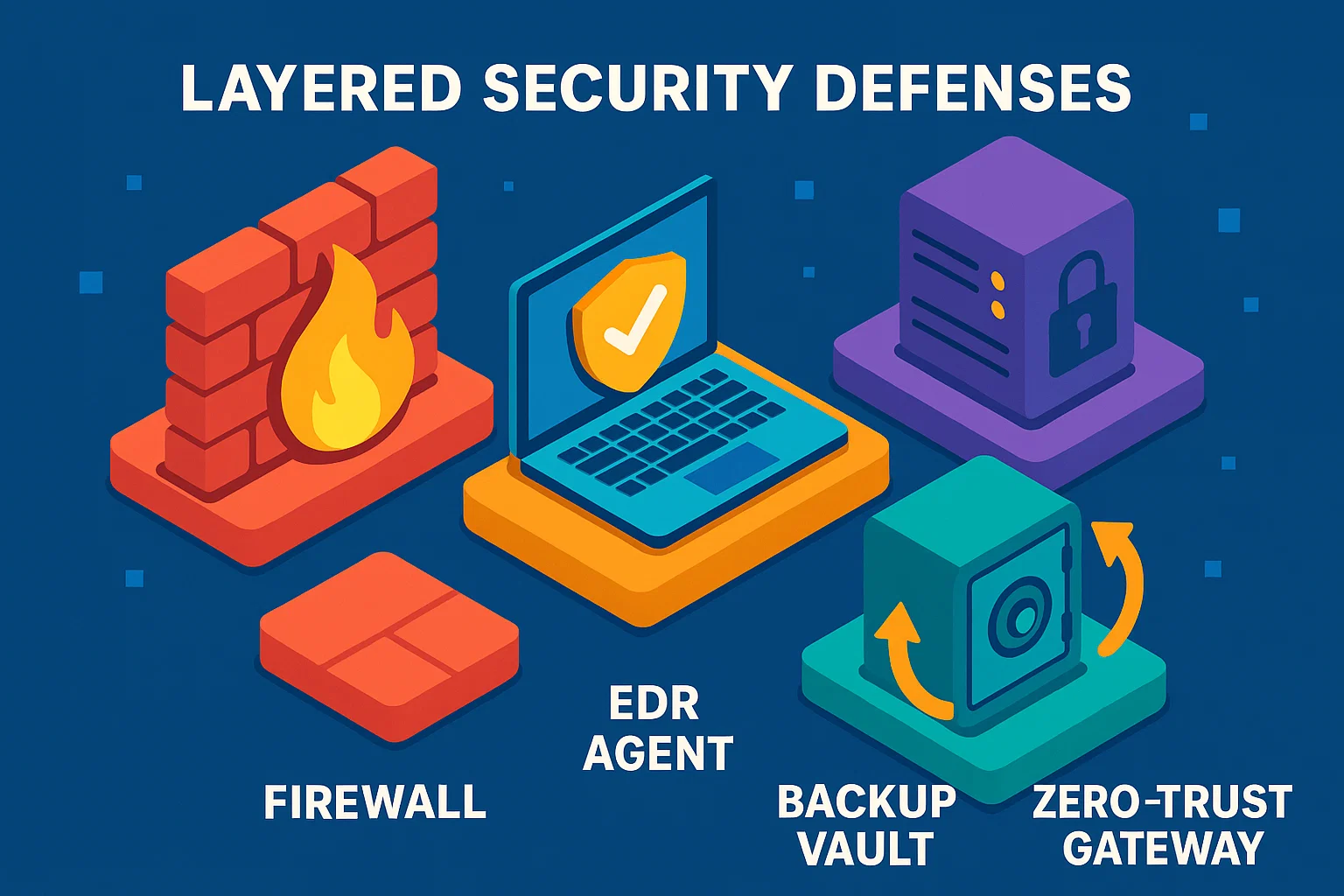
1 – Foundation First: The Bedrock of Ransomware Defense Tips
Think of these five basics as the house rules. Ignore them and no fancy AI sensor will save you.
- Offline, diversified backups. Follow the 3-2-1 gospel—three copies, two media, one off-site. My own Synology backs up to a USB drive that lives unplugged in the closet. ransomware defense tips rule #1.
- Antivirus or EDR that actually updates. “Install and forget” is a myth. Set daily definition pulls at 2 a.m. so nobody complains about lag.
- Patch within 24 hours. EternalBlue is ancient, yet SMB v1 scanners still nail unpatched servers every day. Automate Windows Updates and
apt-getschedules. - Close noisy ports. 135, 139, 445, 3389—if you need them externally, use a VPN or restrict to a single IP. Or better, toss RDP behind a bastion.
- Strong passwords + MFA everywhere. Twelve characters minimum, complexity, and a TOTP prompt for admins. Yes, even the lab VM you swear isn’t critical.
2 – Laser-Focused Ransomware Moves
These ten ransomware defense tips stop the encryption crew before they start throwing AES.”
- Specialized anti-ransomware agents. Tools like 360’s “NSA Immunization” block known exploit chains.
- Lock down SMB shares. Need access? Give read-only. Need write? Scope to a single service account.
- Mail-gateway sandboxing. Strip macros and send weird attachments to a detonated VM.
- Disable Office macros by default. Legit macros sign with certs; everything else dies.
- Show full file extensions. No more “invoice.pdf.exe” tricks.
- Immutable backup snapshots. Object-lock S3 or Btrfs snapshots that ransomware can’t delete.
- Block known ransomware TLDs. Feed threat-intel IOC lists into DNS filtering.
- Stage a phishing tournament. Reward whoever spots the fake billing email fastest.
- Geo-IP isolation. If you only sell to Canada, why allow inbound RDP from who-knows-where?
- Detonation canary files. Seed honey-files and fire alerts on the first encrypt attempt.
3 – Cryptominer Countermeasures
Malicious miners want your CPU/GPU cycles. Kill their supply with the next five ransomware defense tips.
- Watch CPU/GPU telemetry. Alert if either spends 60 seconds over 90 % outside business hours.
- Audit scheduled tasks + crontabs. Fancy-named scripts running from
/tmp? Ax ’em. - DNS egress blocklists. Outbound calls to
xmrpoolornicehash? Drop instantly. - SSH hardening. Key-only auth, non-standard port,
AllowUserslist, and disable root login. - Container network segmentation. Don’t let a rogue pod pivot to your GPU farm.
4 – Ops & Culture Hacks
Security isn’t just tooling—it’s habits. Here are five culture-centric ransomware defense tips that pay dividends.
- Principle of least privilege. Break glass accounts aside, nobody needs Domain Admin.
- Centralized logging & threat hunting. Pipe logs to ELK; schedule weekly hunts for new DLLs under
C:\ProgramData. - Quarterly red-vs-blue drills. Let your pentest team fire Metasploit; fix what they burn.
- Supply-chain scrutiny. Validate software signatures and SHA-256 before install.
- Monthly staff training. Pizza, soda, and a “spot the phishing email” contest keeps eyes sharp.
5 – Response & Recovery Playbook
When smoke rises you need ransomware defense tips that switch from prevention to triage—fast.
- Immediate isolation. Pull the network cable before you Google the error message.
- Deep scans & rootkit checks. PowerTool, GMER, Velociraptor—pick your poison, find the hidden hooks.
- Forensic imaging. Clone drives and RAM dumps for later; never poke live evidence.
- Consult decryption projects. Check No-More-Ransom before even thinking of paying.
- Rebuild, harden, document. Nuke from orbit, reinstall, disable SMB v1, revise firewall rules, celebrate with caffeine.
6 – Advanced Arsenal for 2025 & Beyond
These last five ransomware defense tips lean futuristic but are shockingly accessible.
- EDR + NDR synergy. Correlate endpoint behavior with wire-level anomalies to catch two-stage attacks.
- Zero trust everywhere. “Assume breach” sounds gloomy, but dynamic policy means crypto-nerds can’t laterally move.
- AI-driven anomaly detection. Baseline user keystroke speed; alert when the CFO suddenly pastes 10 MB of PowerShell.
- Blockchain audit trails. Immutable logs for legal hold and blame-free post-mortems.
- Live threat-intel feeds. Auto-ingest IoCs every hour and push to firewalls in real time.
Personal Anecdote Wrap-Up
I once ignored my own ransomware defense tips on a test lab, thinking “It’s isolated, who cares?” Two weeks later the box was overheating because a sneaky cryptominer maxed the GPU while encrypting old VMware images. Lesson learned: practice what you preach. If you adopt even a dozen of these 30 tactics, you’ll sleep a lot easier.
Need a place to start? Make backups tonight. Our step-by-step Windows 11 System Backup guide walks you through a no-sweat imaging routine. And if you’re tuning endpoints for speed as well as safety, check out this Windows 10 performance optimization playbook.
For deeper frameworks and government-grade checklists, skim CISA’s Stop Ransomware portal—it’s free and updated weekly.
Stay safe, patch often, and may your logs be ever boring.

 FoxDoo Technology
FoxDoo Technology