15
Tips
FoxDooTech's Tips category provides practical tech advice, step-by-step how-to guides, tutorials, and useful tips for startups, AI, apps, gaming, and development.

Python automation scripts changed my workday rhythm. A few months back, I had a stack of spreadsheets, a pile of scanned invoices, and a boss who wanted “one neat report by 5 PM.” I brewed a questionable espresso, opened VS Code, and stitched together a tiny toolkit. Two hours later, everything clicked—files merged, PDFs renamed, images shrunk, and a neat contract set printed. Since that week, I’ve kept a folder of bite-size utilities ready to fire. This guide is that folder, cleaned up for you. We’ll mirror a simple structure for each task: the scenario, a clean script, and the thinking behind it. I’ll offer light upgrades so you can adapt fast. And because these Python automation scripts are meant...

I still remember the night Claude saved my hide. Payroll locked at dawn, our API gateway was spitting 502s like popcorn, and my eyelids weighed a metric ton. One desperate prompt later, Claude Code Tips slapped a clean patch into my repo before the coffee even cooled. That caffeine-soaked epiphany sparked the guide you’re reading now. Buckle up—we’re about to unpack ten field-tested tricks that make Claude feel less like a novelty toy and more like the senior engineer you wish you could hire. 1. Write a Rulebook with claude.md Picture this: you onboard a junior dev without documentation. Chaos, right? Claude’s no different. Drop a claude.md file at the project root outlining coding standards, branch strategy, and a “think-plan-check”...

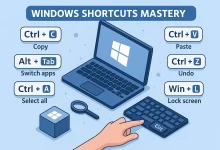
Windows Shortcuts Mastery changed my life one caffeine-fueled night when my mouse died mid-presentation and I survived on Alt + Tab acrobatics. Since then I’ve logged thousands of keystrokes testing, scripting, and (occasionally) abusing every built-in hotkey Windows 11 hides. This guide packs 50 real-world examples—each paired with a plain-English function breakdown—so you can ditch the click-fests and work at warp speed. Why Windows Shortcuts Mastery Still Matters in 2025 Every round-trip from keyboard to mouse costs ~700 ms. Multiply that by 4 000 interactions a day and you’ve burned an hour. These shortcuts shrink UI latency, slash repetitive-strain clicks, and keep your hands on the keys where they belong. Ground Rules: How to Train Shortcut Muscle Memory Practice ten new...

Windows 10 performance starts with the services that launch in the background. Each one consumes a slice of CPU time, RAM and sometimes aggressive disk I/O. Trim the fat, and the operating system feels snappier overnight. Fail to curate them, and even an SSD can start to feel like a spinning platter from 2010. Why Background Services Quietly Dictate Everyday Speed Unlike startup apps—which are easy to find in Task Manager—Windows Services run under the hood, often as SYSTEM. Because they are initialized long before you log on, they can monopolize resources at the exact moment you expect the desktop to spring to life. The impact grows worse on: Machines with 4 GB RAM or slower dual‑core CPUs Laptops thermal‑throttled by quiet fan curves Systems...

Dual-Band WiFi Setup: Should You Merge or Separate SSIDs? In today’s connected world, choosing the best dual-band WiFi setup can make a dramatic difference in performance, coverage, and stability. As more devices compete for bandwidth, deciding whether to merge your 2.4GHz and 5GHz bands under one SSID or keep them separate has become a hot topic among home users and tech enthusiasts alike. Understanding 2.4GHz vs 5GHz WiFi Bands Before diving into the pros and cons of a dual-band WiFi setup, it’s crucial to understand the key differences between 2.4GHz and 5GHz frequencies: Coverage Distance: 2.4GHz signals travel further and penetrate walls more effectively because of their lower frequency. This makes them ideal for larger homes or spaces with multiple...

Lost your Windows 10 product key somewhere between the depths of your messy desktop drawers and the back of that dusty notebook? Fear not, digital explorer! Whether you’re planning a clean install, troubleshooting activation headaches, or just curious about how your PC’s license magic works, this guide will have you uncovering your 25-character Windows 10 key faster than you can say “Tech-savvy hero.” We’ll walk through four different methods—each with its own flair—so you can pick your favorite and get back to conquering the digital world. Let’s dive in! 1. The Command Line Treasure Hunt If you love feeling like a cyber pirate searching for buried treasure, the Command Prompt (or PowerShell) method is for you. In just a single...

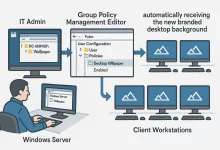
How I Centralized Our Desktop Wallpaper with Active Directory GPO As the IT administrator for one of our corporate clients, I was recently tasked with standardizing the desktop background on nearly 200 domain-joined PCs. Manually updating each machine would be a logistical nightmare, so I leveraged our Windows Server’s Active Directory and Group Policy to automate the process. Scenario & Requirements The client wanted a branded 1920×1080 wallpaper across all employee workstations without touching individual machines. To prepare, I gathered: A high-resolution wallpaper file (1920×1080) to enforce on all desktops. An Active Directory domain controller with file-share capability. Verified AD health (DNS, replication) and appropriate GPO editing permissions. Step 1: Create & Share the Wallpaper Folder On the domain controller:...

How I Transformed Our File Sharing Workflow with Snapdrop In my role as an IT engineer, I encounter daily requests for transferring large design assets, logs, and multimedia between team members. USB drives require manual handoffs, emails choke on attachments over 25 MB, and Bluetooth can take minutes for just one file. Apple’s AirDrop is convenient—if all devices are Apple—but our environment spans Windows, Linux, Android, and iOS. I needed a truly universal solution, and that’s when I discovered Snapdrop. Background: Limitations of Traditional Methods Before Snapdrop, our team struggled with: USB Drives: Risk of lost or infected devices. Email Attachments: Size limits and slow uploads. Bluetooth: Tedious pairing and slow transfer speeds. What Is Snapdrop? Snapdrop is an open-source,...

As an IT professional, one of the constant challenges I face is managing suspicious files and spam emails within our company. Often, these emails or attachments might look legitimate but could easily contain hidden malware that could put our network and data at risk. That’s where Windows Sandbox comes into play—a simple yet powerful solution I rely on daily. Why Choose Windows Sandbox? Windows Sandbox is essentially a lightweight, isolated desktop environment, perfect for safely testing files and links without risking your main operating system or network. Once you close the Sandbox, everything inside it is permanently deleted, making it ideal for handling uncertain files. My Step-by-Step Approach to Testing Files in Windows Sandbox 1. Enabling Windows Sandbox First things...

As a blogger who’s spent countless hours refining my approach to SEO, I’ve noticed one consistent truth: mastering SEO isn’t just beneficial—it’s essential. Here’s why: Why Every Business Needs SEO SEO (Search Engine Optimization) is not just tech jargon—it’s a strategic mix of technology and content designed to attract precise traffic to your website. It builds a three-dimensional matching model aligning user needs, content value, and technical compatibility. Here’s the practical payoff: Traffic Gains: Reach targeted customers and boost your brand search visibility by up to 45%. Cost Efficiency: Cut your CPC expenses by 70% and increase your organic traffic to over 60% of your total visits. Authority & Trust: Achieve top-3 search rankings, building credibility and accumulating valuable backlinks....


 FoxDoo Technology
FoxDoo Technology
 FoxDoo Technology
FoxDoo Technology