Enterprise Network Deployment only gets real when the outsourcing crew’s Sharpie marks become a purchase order. In Part 1 we nailed discovery; now we—an external managed-service provider, not the client’s internal IT squad—must transform raw business objectives into a blueprint that survives board scrutiny, procurement trench warfare, and 3 a.m. failovers. Grab coffee; this is where reputations are forged.
Anchor Every Design Choice to Business Outcomes
Our outsourcing contracts rise or fall on KPI dashboards, not pretty Visio art. Before a single topology sketch, we lock three driver tables:
- Revenue-Critical Flows – payment gateway, real-time analytics, click-and-collect APIs.
- Risk Posture – regulatory penalties, brand damage tolerance, ransomware recovery RTO.
- Growth Velocity – number of sites per quarter, cloud-migration cadence, M&A pipeline.
We tag each driver with a design lever (latency, packet loss, hostname isolation) and a cost lever (CapEx, OpEx, contract penalties). This living matrix sits on Jira backlog ticket ARCH-001; every future pull request must cite which driver it satisfies. It’s ruthlessly simple and keeps Enterprise Network Deployment honest.
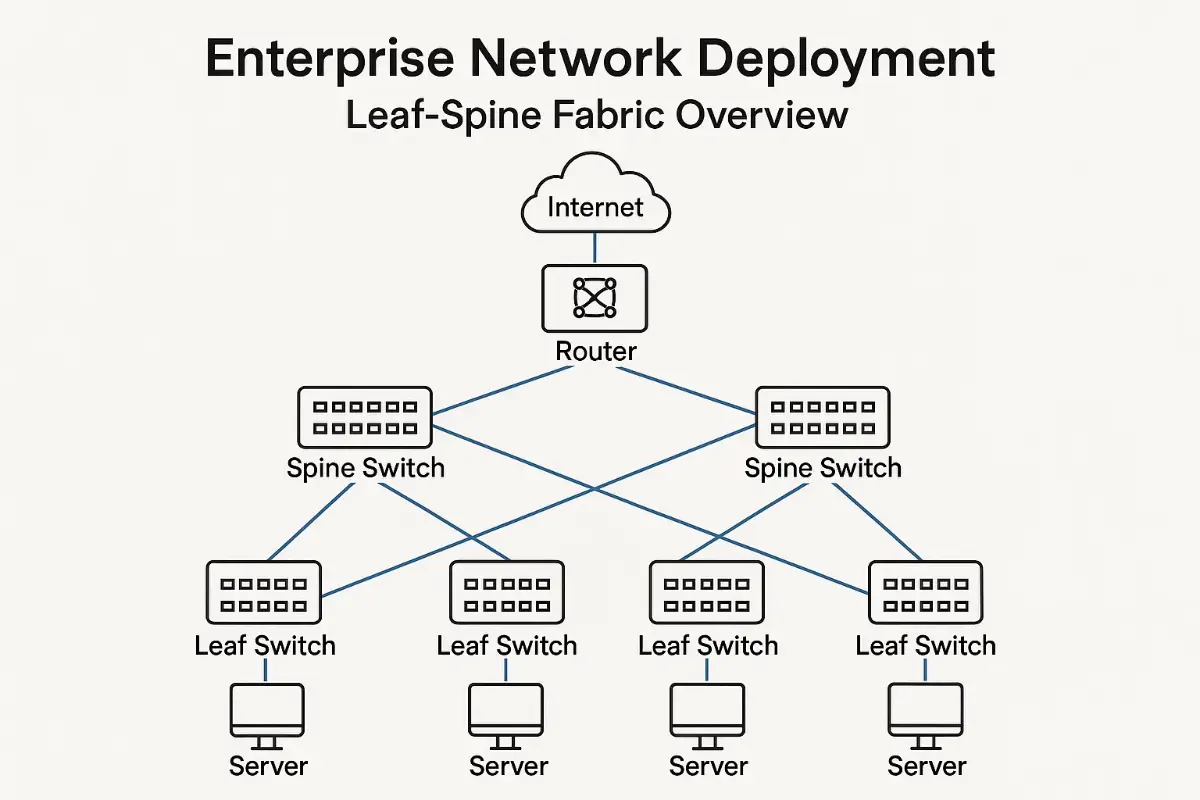
Select the Core Topology: Three-Tier, Leaf-Spine, or Overlay Mesh
In outsourcing land, time-to-deploy equals billable revenue. We offer a prescriptive menu, tuned by hundreds of prior rollouts:
- Three-Tier Campus – core, distribution, access. Best when the enterprise still runs thick-client ERP and has cabling legacy that would make an archaeologist weep.
- Leaf-Spine Fabric – our default for green-field DC builds and container platforms. Horizontal scale, deterministic 3-hop latency, and clean Layer-3 ECMP.
- Overlay Mesh (EVPN / SR-v6) – the big gun for multinational mergers. Lets us bolt disparate data-centers and clouds into one policy fabric without forklift upgrades.
We prototype each option in an Infrastructure-as-Code test harness. If the CFO chokes on optic counts, we downshift port speeds only if it doesn’t shove us outside SLA jitter targets.
WAN Choices: Dual DIA, MPLS, SD-WAN or SASE—Why Not All Three?
Enterprises rarely let us kill MPLS outright—too many SLA clauses. So our go-to Enterprise Network Deployment stack looks like this:
- Primary circuit: 1 Gb MPLS with strict CoS buckets for transactional flows.
- Secondary circuit: DIA fiber into our SD-WAN overlay for SaaS and video.
- Tertiary circuit: 5 G router on rooftop for break-glass failover and Day-1 store pop-ups.
The SD-WAN controller (we favor Versa or Fortinet depending on existing spend) steers traffic via dynamic-path-selection policies. If jitter on MPLS exceeds 20 ms, payments jump to DIA until the carrier ticket closes. We demo this in the lab, screenshot the live failover, and email it to the legal team—nothing calms attorneys faster than proof.
Zero-Trust Fabric: Identity over IP
Because we’re the outsourcer, we must assume every packet might come from an adversary inside the client’s address space. Our security fabric therefore:
- Starts with certificate-based 802.1X on every port and SSID.
- Maps user/device to a security group tag (SGT) or VRF; traffic hits an inline policy node within 50 µs.
- Uses Cisco SD-Access micro-segmentation or Aruba CX Dynamic Segmentation for east-west isolation.
- Extends to branches via Cloudflare Zero Trust gateway pop-outs, shrinking the threat radius globally.
This identity-driven stack appears in our Statement of Work under “Deliverable: Zero-Trust Enforcement Plane”. Pen testers from the client’s red-team poke it later; our bonus hinges on their findings.

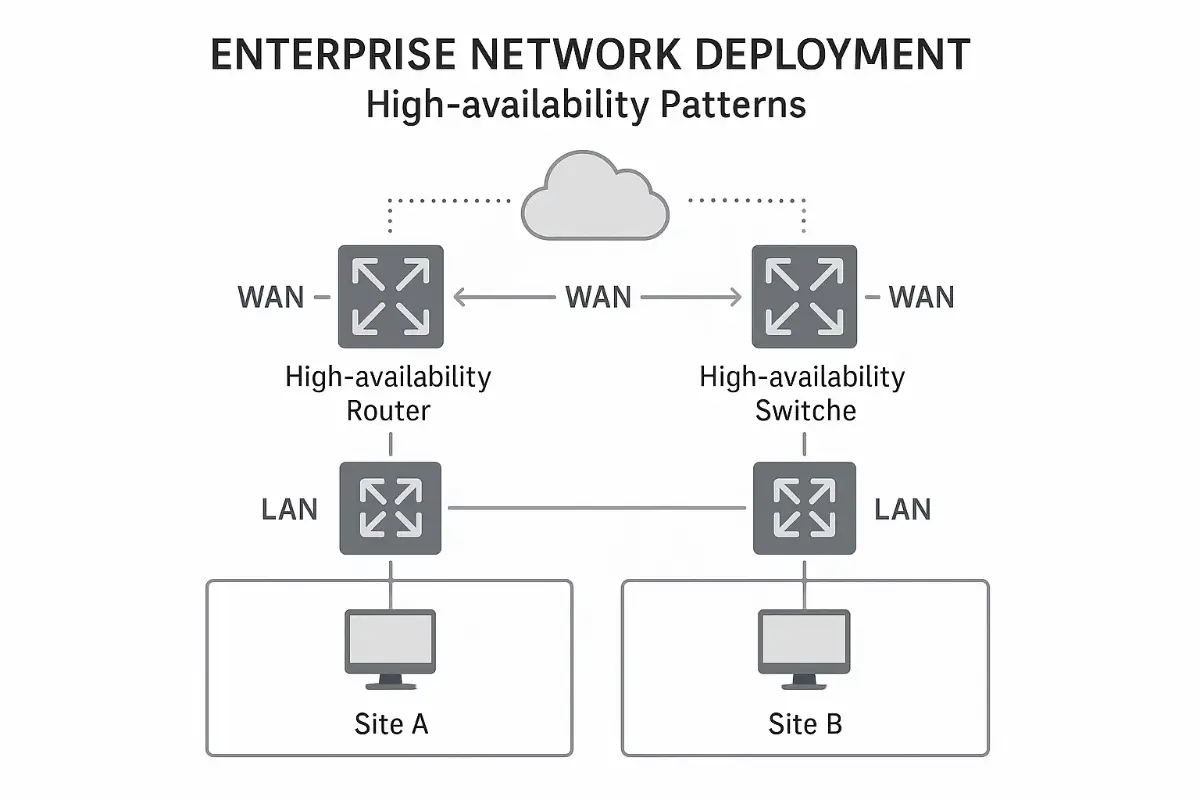
High-Availability Patterns Outsourcers Swear By
We accept liquidated damages for downtime, so redundancy is religion:
- Dual Sup Engines – supervisor hot-swap in core chassis.
- Multichassis Link Aggregation (MLAG) – ToR pairs feed every server; a single switch failure must not sever a vNIC.
- Per-rack UPS plus dual PDUs; we audit breaker panels for hidden single points.
- Path Diversity – a fiber trencher once killed both WAN legs on a campus. Lesson learned: insist on conduit maps and physically divergent splicing.
We stage full power-pull tests in a dark launch window, record video, and deliver it as evidence that the design—versus mere theory—meets Enterprise Network Deployment resilience goals.
Scalability Roadmap: From 25 G to 400 G Without Forklift Pain
Every big enterprise swears growth will be “steady.” Then a viral product drops, and link graphs look like rocket ascents. Our safeguard:
“Design for double the three-year traffic projection, then show the cost delta; let the board decide.”
The roadmap table:
| Tier | Now | Year +1 | Year +3 |
|---|---|---|---|
| Access | 10 G | 25 G | 25 G breakouts |
| Spine | 100 G | 200 G | 400 G PAM4 |
| WAN | 1 Gb MPLS | 2 Gb active-active | 10 Gb wavelength |
Because optics cost spikes exponentially, we pre-install only the cages and blank plates. When the trigger metric (≥ 60 % average link load over 30 days) fires, procurement orders the transceivers. Keeps CapEx lean, keeps Enterprise Network Deployment nimble.
Automation Pipeline: Git-Driven Networks or Bust
Manual configs wreck SLAs. Our outsourcing toolkit:
- GitLab CI for intent files (
.yaml) tagged per site. - Nornir + Ansible blend: Nornir for inventory filtering, Ansible for idempotent pushes.
- PyATS tests every commit on a containerized lab; failures block merge.
- HashiCorp Vault provides one-time tokens so techs never see device passwords.
We embed this flow in the Master Services Agreement annex; clients pay extra for “self-service” merge rights. Suddenly, change windows shrink from hours to minutes and everyone sleeps better.
Multi-Vendor Matrix: Bargaining Chip & Risk Hedge
The finance VP wants price leverage; the CISO wants code diversity against supply-chain attacks. We deliver both with a transparent vendor matrix:
| Capability | Primary | Secondary | Fallback |
|---|---|---|---|
| Spine Switch ASIC | Broadcom Trident | Intel Tofino | Marvell Prestera |
| SD-WAN Edge | Fortinet 61F | Versa CSG1000 | Peplink Balance 580 |
| Firewalls | Palo Alto PA-440 | Check Point Quantum 1570 | SonicWall TZ470 |
Each option passes a feature parity test scripted in json-schema. If the primary SKU hits supply-chain delay, procurement flips to secondary with minimal doc edits—a lifesaver when chip shortages strike.
Documentation & Handoff: Make it Foolproof
Outsourcers don’t get infinite onsite time. We package:
- Architecture Design Document – 150 pages, diagrams generated from NetBox.
- Run-Book – step-by-step CLI and GUI for routine tasks.
- Day-2 Playbooks – common incidents (link flap, SD-WAN route loops) with decision trees.
- Change Control Templates – pre-filled with rollback commands.
All files live in a customer-facing Confluence space with SAML SSO. The client’s NOC can self-serve, but our 24 × 7 ops desk remains contractually responsible. That clear boundary keeps escalations sane.
Field Story: The 72-Hour Airport Build
I’ll never forget a last-minute bid from an airport authority: “We open Terminal D in three days, can you make Wi-Fi and flight boards talk?” Internal IT was overloaded, so our outsourcing squad landed with pre-staged leaf-spine racks, SD-WAN CPEs flashed in the van, and an Ansible tower tethered to 5 G. By hour 70 the first boarding groups walked through, blissfully unaware. That miracle happened only because our architecture kit—redundant fabrics, portable DHCP stack, zero-trust overlay—was modular and pre-scripted. Win the design game and deployment speed follows.
Further Reading Before Part 3
Sharpen your hardware acumen with our IT Operations Equipment pro secrets, then brace for OS meltdown scenarios in Windows 11 Black Screen of Death. Both guides dovetail with choosing resilient gear and endpoint failover logic for your next Enterprise Network Deployment.
Lock these architecture moves today, and when Part 3—Implementation Roadmap—drops, you’ll hit the ground running with zero surprises and a boardroom grinning at SLA charts.

 FoxDoo Technology
FoxDoo Technology