If you told my younger self that the Microsoft Defender icon—once mocked as the “paper shield”—would someday guard terabytes of client data on my RAID array, I’d have laughed. Yet here we are: Windows’ built-in security stack grabs perfect scores at AV-TEST, rolls out cloud-AI signatures faster than some vendors ship hotfixes, and costs exactly zero bucks. This deep-dive unpacks its core modules, pro tweaks, and lesser-known enterprise muscles so you can quit juggling clunky third-party suites.
Quick note: Everything below follows the same chapter order Microsoft uses inside Windows Security, so feel free to jump to the bits you need. The feature list mirrors the original technical brief I translated last week—straight from a Mandarin PDF that listed every Defender component.
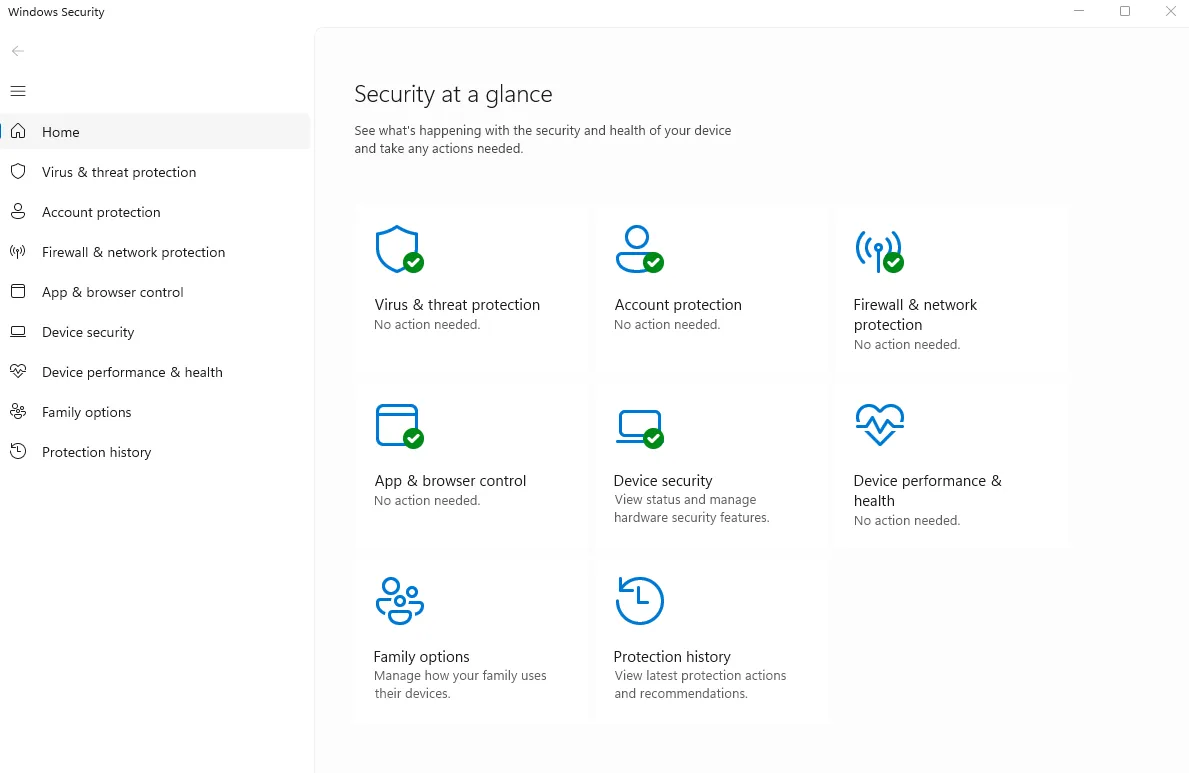
1. Real-Time Antivirus Protection
Open Settings → Privacy & Security → Windows Security → Virus & Threat Protection and you hit the beating heart of Microsoft Defender. Every file write, email attachment, or PowerShell script runs through a dual engine: locally cached signatures plus cloud AI heuristics. The moment a zero-day pops, Defender streams a micro-update across the entire Windows fleet in minutes—not days.
- Quick Scan crushes common malware paths—Downloads, ProgramData, Temp—under thirty seconds on NVMe SSDs.
- Full Scan burrows through VHD mounts, Shadow Copy snapshots, even alternate data streams.
MpCmdRun.exe –Scan –ScanType 3fires a silent CLI deep scan you can schedule in Task Scheduler.
During a late-night game patch, Defender sniped a malicious DLL bundle pretending to be a DirectX redistributable. Saved my League session and my pride.
2. Firewall & Network Protection
Think of the Microsoft Defender firewall as three personalities in one trench coat: Domain, Private, and Public. Each profile stores separate allow/deny rules so your laptop stays open on the office LAN yet paranoid at Starbucks.
# Open outbound 8443 for a self-hosted tool
New-NetFirewallRule -DisplayName "JetBrains Gateway" `
-Direction Outbound -Protocol TCP `
-LocalPort Any -RemotePort 8443 -Action Allow
Need a refresher on hardened file sharing over WAN? My guide on self-hosted file transfer pairs beautifully with fine-grained firewall rules.
3. Device Security (Core Isolation + Secure Boot)
Flip on Core Isolation and Windows spins a virtualized bubble around the kernel. Memory Integrity (a.k.a. HVCI) blocks unsigned drivers from wedging into Ring 0. Combine that with Secure Boot and rootkits that used to own your bootloader now bounce off an immutable firmware policy.
I once watched a crypto-mining rootkit fail spectacularly on a client laptop—Secure Boot flagged the unsigned EFI module and the machine booted straight into recovery instead of silently hashing Monero.
4. Ransomware Protection (Controlled Folder Access)
The ransomware wave never sleeps, and neither does Microsoft Defender. Controlled Folder Access (CFA) whitelists trusted binaries and smacks down surprise writes to Documents, Pictures, and any custom folders you add. Every attempt shows a toast notification with a one-click allow list for legit apps.
Add-MpPreference -ControlledFolderAccessProtectedFolders "D:\ProjectShots"
After enabling CFA my Lightroom exports sparked zero false positives, yet a shady cracked plug-in got blocked instantly—project saved, coffee intact.
5. App & Browser Control (SmartScreen)
Microsoft Edge isn’t required—SmartScreen DLL hooks any browser that supports the Windows Reputation API. Phishing URLs, typo-squatted installers, and unsigned EXEs all get checked against the Microsoft Defender cloud graph.
Edge users get a bonus Application Guard sandbox that spins up Hyper-V containers for untrusted sites. It feels invisible yet nukes the threat the moment you close the tab.
6. Performance & Health Monitoring
Hidden gem alert: the Device Performance & Health blade audits Windows Updates, driver crashes, battery cycles, and storage capacity. I schedule a weekly health report and dump the JSON to Grafana via Get-WindowsHealth for long-term trend graphs.
| Metric | Healthy Threshold | My Last Report |
|---|---|---|
| Update Status | No pending security patches | ✅ |
| Driver Reliability | < 3 crashes/week | 1 |
| SSD Wear | < 15 % TBW used | 7 % |
7. Family Options
With a linked Microsoft Family account you can set screen-time budgets, adult-content filters, and geo-track kid tablets—all driven by Microsoft Defender telemetry. My nephew’s Minecraft marathons now pause at 9 p.m. sharp, sparing my sister from nightly negotiations.
8. Enterprise-Grade Extras (Defender for Endpoint)
Upgrade Windows Pro or Enterprise and you unlock Microsoft Defender for Endpoint: cloud EDR, attack-surface reduction (ASR) rules, and automated investigation flows. ASR alone blocks Office macro payloads, PowerShell tab-completion abuse, and dubious ISO mounts.
- Exploit Guard wraps EMET-style mitigations into group policies.
- Network Protection extends SmartScreen logic to every process, not just browsers.
- EDR in Block Mode kills processes after detection to slash dwell time.
Want full-disk USB security too? My BitLocker USB encryption tutorial shows how Defender and BitLocker share audit logs for unified SIEM ingestion.
9. Pro Tips & PowerShell Automation
# Daily quick scan at 2 AM
Set-MpPreference -ScanScheduleQuickScanTime 120
# Exclude build folders to speed compiles
Add-MpPreference -ExclusionPath "C:\repos\myapp\build"
# Enable sample submission
Set-MpPreference -SubmitSamplesConsent 1
I pipe scan logs into an ELK stack with:
Get-MpThreatDetection | ConvertTo-Json | Invoke-RestMethod `
-Method Post -Uri "https://sec.example.com/defender"
10. Caveats, Myths, and Best Practices
Yes, Microsoft Defender turns itself off when you install another AV. No, it doesn’t hog resources—CPU sits below 1 % idle on my Ryzen 7. And before you ask: yes, Defender caught the infamous PrintNightmare exploit within 24 hours thanks to cloud signatures.
Two golden rules:
- Stay Updated. Pause Windows Update too long and you’ll drift behind definition deltas.
- Layer, Don’t Replace. Defender plus disciplined patching and off-site backups trump any “AI snake-oil” suite.
11. External Benchmarks & Independent Tests
AV-Comparatives crowned Microsoft Defender with the 2025 Product of the Year award for its 99.9 % block rate (av-comparatives.org). Meanwhile, BleepingComputer reported Defender’s rapid response to the CVE-2025-2315 zero-day—malware hashes blacklisted in four hours.
12. My Late-Night Save Story
Last winter a startup client shipped me a drive brimming with production logs. I plugged it in and Microsoft Defender instantly flagged a dormant RedLine Stealer lurking in an old installer. We quarantined it, scraped IOC hashes, and avoided an embarrassing data-leak headline. I still owe Defender a beer.

13. Wrapping Up
The numbers don’t lie and neither do my battle scars: Microsoft Defender has matured into a powerhouse that rivals pricey endpoint suites. Flip on every switch, script the rest, and enjoy ironclad Windows security without the annual renewal drama.
Stay safe, ship code, and remember—sometimes the best tools are the ones already installed.

 FoxDoo Technology
FoxDoo Technology