I still remember hauling a beige 802.11b PC-Card to a coffee shop in 2001—thrilled about “11 Mbps” while my dial-up friends stared in envy. Fast-forward to last month when I pushed 3 Gbps over WiFi 6E during a VR demo and nobody blinked. That dizzying leap is exactly why understanding WiFi Generations matters more than ever. WiFi Features & Core Fundamentals Every WiFi Generations release inherits three promises: untethered access, vendor interoperability, and backward compatibility. But the devil lives in PHY advances—modulation, coding, and antenna math that decide whether your Zoom stays crisp or crumbles. Wireless freedom via 2.4 GHz, 5 GHz, and now 6 GHz ISM bands. Plug-and-play scale—one SSID can host dozens of laptops, cameras, sensors. Standards governance...

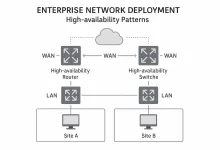
Enterprise Network Deployment doesn’t end when LEDs turn green. The real scorecard starts on “Day 2+”—that long haul where uptime, speed, and cost efficiency either make heroes of outsourcing teams or send CFOs hunting new vendors. Building on our Part 3 go-live victory lap and the iron-clad security fabric from Part 4, this final chapter dives deep into the gritty, coffee-fueled world of post-deployment operations. Grab that mug; we’re gonna keep this network humming. Define the Operational Charter: Who Owns What After Go-Live? Before the confetti lands, nail down an Operational Charter that maps every Enterprise Network Deployment component to a named owner and KPI. Our managed-service provider (MSP) contract usually splits duties: MSP NOC: 24 × 7 monitoring,...

Enterprise Network Deployment isn’t truly “done” when the links come up—it’s secure when every hostile packet dies at the perimeter and inside the fabric. After hammering through discovery, architecture, and implementation in Parts 1-3, our outsourced MSP crew now shoulders the heaviest crown: building a security posture that survives auditors, red-team drills, and next month’s zero-day headline. Why Zero-Trust Is Non-Negotiable for Outsourced Deployments When a giant enterprise hires us instead of leaning on its own IT squad, it’s betting that we’ll spot and squash threats faster than an in-house team juggling ten other projects. Zero-trust gives us that edge because identity becomes the new perimeter—users, devices, and apps must prove themselves at every hop. Think of it as...

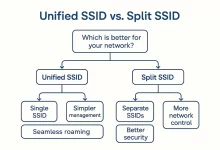
Dual-band WiFi can feel like a magic carpet ride—or a rush-hour traffic jam—depending on one make-or-break choice: do you blend 2.4 GHz and 5 GHz under a single SSID or split them apart? As an IT outsourcing crew that lives or dies on service credits, we’ve watched too many clients face-plant because they copied the default wizard. This guide unpacks the nine fatal traps we keep bailing folks out of and hands you a battle-tested decision blueprint. Preface: The Coffee-Shop Myth Last winter I helped a boutique law firm troubleshoot “random WiFi freezes.” The junior admin swore unified SSIDs were best practice—because that’s how his home router shipped. Cute. Two hours and twenty Wi-Fi analyzers later we discovered every iPhone...

Enterprise Network Deployment gets brutal once gear leaves the warehouse. In this part of the playbook we act as the external managed-service provider who owns every SLA and every panic call—not the client’s internal IT crew. Our mission: transform the signed architecture from Part 2 into blinking LEDs, routed packets, and a cutover that feels boring (because boring means nothing broke). Project Mobilization & Supply-Chain Logistics The clock starts the second the purchase order lands. We immediately spin up a Mobilization War-Room in Jira with three swim-lanes: Procurement + Shipping – track lead times, pallet weights, customs docs. Staging + QA – prep configs, burn-in tests, compliance labels. Field + Cutover – site access windows, lift-gate trucks, hot spares....

Enterprise Network Deployment only gets real when the outsourcing crew’s Sharpie marks become a purchase order. In Part 1 we nailed discovery; now we—an external managed-service provider, not the client’s internal IT squad—must transform raw business objectives into a blueprint that survives board scrutiny, procurement trench warfare, and 3 a.m. failovers. Grab coffee; this is where reputations are forged. Anchor Every Design Choice to Business Outcomes Our outsourcing contracts rise or fall on KPI dashboards, not pretty Visio art. Before a single topology sketch, we lock three driver tables: Revenue-Critical Flows – payment gateway, real-time analytics, click-and-collect APIs. Risk Posture – regulatory penalties, brand damage tolerance, ransomware recovery RTO. Growth Velocity – number of sites per quarter, cloud-migration cadence,...

Enterprise Network Deployment isn’t about racks and routers first—it’s about knowing exactly why those racks and routers will exist. As an IT outsourcing partner who lives or dies on SLAs, I’ve sat in more discovery workshops than I can count, from skyscrapers in Chicago to factory floors in Shenzhen. Every winning project shared one secret sauce: a brutally honest, data-driven requirements mapping phase. Skip it and the rollout gets ugly, budgets bloat, and fingers point at the vendor—you. Enterprise Network Deployment Through the Outsourcing Lens When the client’s internal IT team calls us, they’re not just looking for extra hands; they’re looking for outside accountability. Our discovery process has to prove three things up front: We understand the big-picture business...

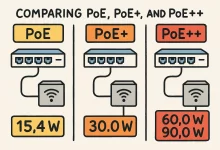
Introduction Picture this: I’m dangling off a ladder at 2 a.m., trying to finish a last-minute security-camera install. Power outlets? None. All I had was a single Cat 6 drop and a trusty PoE switch humming in the rack. One cable—data plus juice—and I was done. That “aha!” moment sold me on power over Ethernet for life. From 2003 to Today—The PoE Timeline The IEEE 802.3af standard officially blessed PoE back in 2003, giving us 15.4 W per port and kicking off two decades of innovation. Demand skyrocketed, so 802.3at (PoE+) doubled the output to 30 W. Fast-forward to the modern 802.3bt era—better known as PoE++—and we’re talking up to 100 W per port for Type 4 devices, enough to...

Dual-Band WiFi Setup: Should You Merge or Separate SSIDs? In today’s connected world, choosing the best dual-band WiFi setup can make a dramatic difference in performance, coverage, and stability. As more devices compete for bandwidth, deciding whether to merge your 2.4GHz and 5GHz bands under one SSID or keep them separate has become a hot topic among home users and tech enthusiasts alike. Understanding 2.4GHz vs 5GHz WiFi Bands Before diving into the pros and cons of a dual-band WiFi setup, it’s crucial to understand the key differences between 2.4GHz and 5GHz frequencies: Coverage Distance: 2.4GHz signals travel further and penetrate walls more effectively because of their lower frequency. This makes them ideal for larger homes or spaces with multiple...

Linux server network troubleshooting is an essential skill for every system administrator responsible for maintaining reliable services. When your server suddenly loses connectivity, experiences slow response times, or refuses to communicate with other machines, your first question often is: “Where’s the issue?” This comprehensive guide will walk you through six of the most frequent network problem scenarios on Linux, complete with practical commands to identify and fix each issue. By following these tips, you’ll be equipped to pinpoint the root causes faster, minimize downtime, and keep your systems running smoothly. Scenario 1: Server Cannot Reach the Public Internet Symptoms: ping www.example.com returns no response curl reports “Could not resolve host” When your Linux server can’t access the public internet, start...


 FoxDoo Technology
FoxDoo Technology FoxDoo Technology
FoxDoo Technology