Enterprise Network Deployment isn’t about racks and routers first—it’s about knowing exactly why those racks and routers will exist. As an IT outsourcing partner who lives or dies on SLAs, I’ve sat in more discovery workshops than I can count, from skyscrapers in Chicago to factory floors in Shenzhen. Every winning project shared one secret sauce: a brutally honest, data-driven requirements mapping phase. Skip it and the rollout gets ugly, budgets bloat, and fingers point at the vendor—you.

Enterprise Network Deployment Through the Outsourcing Lens
When the client’s internal IT team calls us, they’re not just looking for extra hands; they’re looking for outside accountability. Our discovery process has to prove three things up front:
- We understand the big-picture business outcomes—revenue paths, customer experience, compliance risk.
- We can align multi-vendor ecosystems without bias toward any single hardware supplier.
- We own the timeline and the penalties if the network underperforms.
That’s a very different starting line than a corporate IT department redesigning its own turf. We, the outsourcer, carry contractual risk—and that keeps our discovery checklist razor-sharp.
Kickoff Meeting: Setting the Contractual Reality
The kickoff is half pep-talk, half pre-nup. I open with the project charter, but quickly slide the Master Service Agreement (MSA) onto the Zoom screen. Everyone needs to see how service credits trigger and how scope creep explodes cost. We identify the following workstreams:
- Stakeholder Interviews & Business Process Mapping
- Technical Baseline & Gap Analysis
- Security & Compliance Overlay
- Capacity Modeling & Forecasting
- SLA & Risk Matrix Definition
- Formal Requirements Spec Sign-off
This agenda becomes the spine of our shared project notebook in Confluence, updated daily.
Stakeholder Interview Playbook
Interview velocity is everything. I aim to finish forty interviews in two weeks. Here’s the script that saves my bacon:
| Role | Key Questions | Deliverable |
|---|---|---|
| C-Suite Sponsor | “Which revenue streams fail if the network blips for 60 seconds?” | Critical Path Map |
| Plant Manager | “What’s the max jitter your robotic arm tolerates?” | Real-Time Traffic SLA |
| Security Officer | “Which frameworks rule your audit?” | Compliance Control Matrix |
| DevOps Lead | “How many daily deployments? Blue/Green or Canary?” | East-West Bandwidth Chart |
| Facilities | “Any asbestos walls still hiding?” | Cabling Feasibility Log |
I record with Otter.ai (with permission), then run a Python script that word-clouds pain points. “Latency”, “Cloud ERP”, and “Zero-Trust” usually scream out. Those words guide the Architecture phase later.
Technical Baseline: What’s Really Humming?
Enter the war-room weekend. Two engineers and I parachute onsite with Fluke testers, a NUC loaded with nProbe, and a stack of show tech scripts. We map every switch, router, and mysterious “temporary” firewall rule.
# Example baseline script for Cisco & Juniper mix
for device in $(cat inventory.txt); do
echo "**** $device ****"
ssh -o ConnectTimeout=3 $device "show version | include uptime"
ssh $device "show interface counters errors"
scp $device:startup-config backups/$device.cfg
done
The grim truth emerges: half the core switches are EOS next quarter, the WAN routers run decade-old IOS, and there’s an undocumented L2 stretch between two data centers. We note every gap in a Baseline Audit Report—due 48 hours after the onsite sweep.
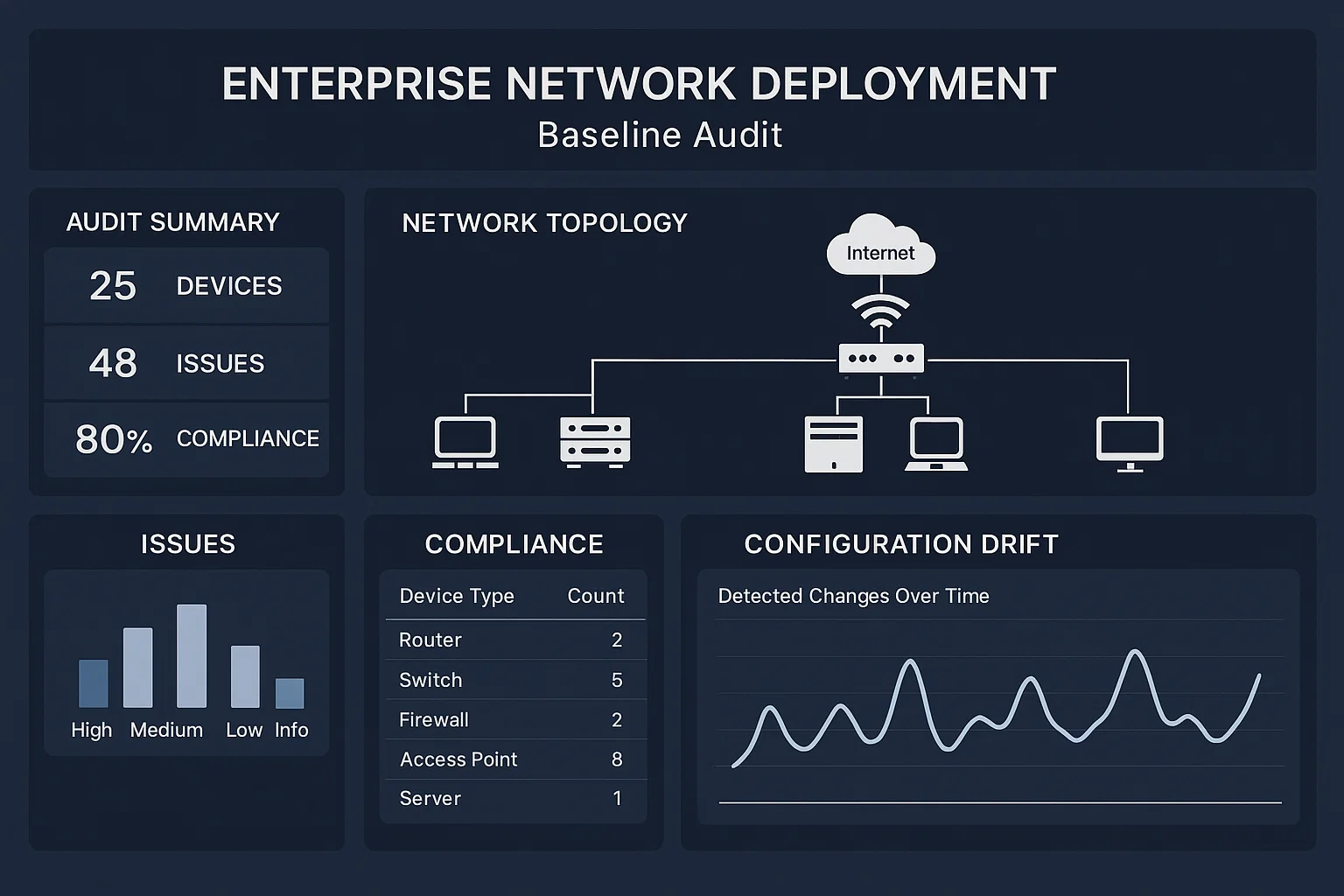
Application & Traffic Mapping
This step makes or breaks Enterprise Network Deployment success for modern enterprises. We:
- Pull 30-day flow logs from existing firewalls.
- Group traffic by application using
ntopngand custom tags. - Chart diurnal peaks and burst ratios.
During a recent retail chain engagement we discovered their click-and-collect app spiked to 80 % of WAN usage right after TikTok promoted a flash sale. Without that nugget we would have under-specced the metro-Ethernet link and eaten SLA penalties every Friday night.
Security & Compliance Overlay
Outsourcers can’t claim ignorance when the auditor knocks. We map each data flow to frameworks like ISO 27001, PCI-DSS, and NIST 800-53. The trick is to avoid theory lectures—clients want concrete tasks. We create a “Controls Traceability Spreadsheet” listing:
- Control ID (e.g., PCI 1.3.5)
- Current Implementation (e.g., Stateless ACLs at DC Edge)
- Gap (e.g., No TLS inspection for POS terminals)
- Remediation Recommendation
We reference Cisco’s Campus & Branch Design Zone segmentation guide to justify our segmentation logic and lean on Cloudflare’s microsegmentation primer within its Zero-Trust learning center when board members ask “Why micro-segments?”
Capacity Forecasting & Growth Scenarios
Enter the spreadsheet marathon. We feed historical traffic into a Monte Carlo model using pandas and fbprophet, then overlay corporate hiring plans and IoT roll-outs. Three scenarios emerge:
- Steady – 12 % CAGR, maintain existing metro-E circuits.
- Expansion – 25 % CAGR plus new branch offices; needs SD-WAN fabric with dual uplinks.
- Disruptive – 40 % CAGR driven by AR/VR support; fiber backbone upgrade mandatory.
The CFO picks Expansion, but signs an addendum accepting budget revisions if Disruptive becomes real. Paperwork now matches physics—no more quarterly surprises.
SLA & Risk Matrix Workshop
Risk talk is where optimism dies and engineering thrives. We paint a classic heat map:
| Failure Mode | Impact | Probability | Residual Risk |
|---|---|---|---|
| Primary DC Power Loss | Critical | Low | Medium |
| Carrier Fiber Cut | High | Medium | High |
| Mis-config Push | Medium | High | High |
For each “High” box we draft mitigations: dual-grid UPS, 4G failover, staged config pipelines. The workshop ends only when every exec signs next to the risk matrix. That signature page is gold during inevitable outage post-mortems.
Consolidating Deliverables: The Requirements Specification
Everything funnels into a single PDF + Excel bundle:
- Statement of Objectives – five bullet business outcomes.
- Network Service Catalog – per-site VLAN, QoS, and security tiers.
- Bill of Materials (Rough-Order) – hardware skus with lifecycle status.
- Gap Analysis Matrix
- Risk & SLA Register
- Appendices – raw configs, flow logs, interview transcripts.
The RS becomes the contractual reference for Architecture & Design (Part 2). Change requests after sign-off trigger scope and price adjustments—protecting both client and vendor.
Common Pitfalls Outsourcers Must Dodge
- Talking Gear Too Soon. Vendors love shiny data-sheets. Resist.
- Underestimating Cabling Deadlines. Plenum-rated fiber has a 12-week lead time in some regions.
- Ignoring Facilities. HVAC and rack space kill designs faster than router buffer overruns.
- Softball Interviews. Ask “What keeps you up at night?” then listen.
- Not Logging Time-Stamps. Discovery hours map directly to billing; sloppy logs breed disputes.
A Quick Anecdote: The 3 A.M. Warehouse Surprise
Two winters ago a logistics giant hired us to “upgrade Wi-Fi”. During midnight discovery we found forklift telemetry running over dusty 802.11b radios. One forklift crashed whenever packet loss hit 20 %. We switched to industrial Wi-Fi 6E APs and cut accidents by 90 %. The client’s ops director now name-drops our firm at every industry panel. Moral? Discovery saves lives, not just packets.
Next Steps & Further Reading
Ready to turn specs into topology diagrams? Stay tuned for Part 2: Architecture & Design next week.
Meanwhile, bone up on endpoint resilience with our deep-dive on Windows 11 Black Screen of Death, or brush up your hardware chops via IT Operations Equipment Pro Secrets. Both guides dovetail nicely with capacity planning decisions.
If you’ve nailed every checklist above, congratulations—you’re already halfway to a bulletproof Enterprise Network Deployment.

 FoxDoo Technology
FoxDoo Technology